A new Ivanti study on patch management shows: Almost three quarters of IT security professionals consider patches too complex and time-consuming. However, a lack of time and the unclear prioritization of vulnerabilities and patches expose companies to risks of cyber attacks.
Ivanti, the automation platform that discovers, manages, secures and maintains IT assets from the cloud to the edge, today published the results of a study on patching. Accordingly, a majority (71%) of IT and security experts find patching too complex, cumbersome and time-consuming. The corona pandemic is also having an impact on the topic: 57% of those surveyed stated that remote work has increased the complexity and scope of patch management. Not least because of this, patching often takes a back seat to other tasks, as 62% of those surveyed stated.
According to the survey, patches cost (too much) time
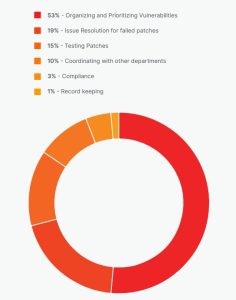
But what exactly do security teams spend their time on patching? 53% of respondents said that managing and prioritizing critical vulnerabilities takes up the majority of their time. In second place is providing solutions to failed patches (19%), then testing patches (15%) and finally coordinating with other departments (10%). The challenges IT and security teams face when patching could be why 49% of respondents find their organization's current patch management protocols insufficient to effectively mitigate risk.
Attackers set the pace
At the same time, the speed at which weak points are used as weapons continues to increase. This is why speed is also an essential factor in defending against attacks. To clarify: It takes an average of 100 to 120 days for companies to roll out an available patch. However, it takes threat actors an average of just 22 days after a vulnerability is published to develop a working exploit, according to an analysis by Rand Corporation.
Johannes Carl, Expert Manager PreSales - UxM & Security at Ivanti, rates the study: “These results come at a time when IT and security teams are confronted with the challenges of the 'Everywhere Workplace': Teams are increasingly distributed - in a whole new dimensions. In this context, ransomware attacks are also increasing, with the corresponding effects on business and politics. Most organizations do not have the visibility or the resources to correlate current threats like ransomware with all of the associated exploited vulnerabilities. The combination of risk-based vulnerability prioritization and automated patch intelligence can reveal vulnerabilities that are actively exploited in connection with ransomware. IT and security teams can seamlessly deploy patches and solve problems that pose a risk to companies. ”The analyst firm Gartner describes risk-based vulnerability management as one of the most important security projects that security and risk management experts will have to prepare for in 2021.
WannaCry targeted unpatched systems
The WannaCry ransomware attack, which encrypted an estimated 200.000 computers in 150 countries, is a prime example of the serious consequences that can occur if patches are not applied in a timely manner. A patch for the vulnerability exploited by the ransomware existed several months before the first attack, but many organizations did not implement it. And even now, four years later, two-thirds of companies still haven't patched their systems. However, organizations around the world are still being hit by WannaCry ransomware attacks; From January to March 2021, the number of organizations affected by WannaCry ransomware increased by 53%. Ivanti interviewed over 500 corporate IT and security professionals in North America and EMEA for the study.
More at Ivanti.de
About Ivanti The strength of unified IT. Ivanti connects IT with security operations in the company in order to better control and secure the digital workplace. We identify IT assets on PCs, mobile devices, virtualized infrastructures or in the data center - regardless of whether they are hidden on-premise or in the cloud. Ivanti improves the provision of IT services and reduces risks in the company on the basis of specialist knowledge and automated processes. By using modern technologies in the warehouse and across the entire supply chain, Ivanti helps companies improve their ability to deliver - without changing the backend systems.