Unit 42, the research team at Palo Alto Networks, has published a research report on a new peer-to-peer (P2P) worm targeting the cloud, dubbed P2PInfect. This worm targets vulnerable Redis systems with container-effective exploits. At the same time, Unit 42 also published a report on Mallox ransomware. The researchers observed a nearly 50 percent increase in activity, with MS-SQL servers being exploited to spread the ransomware.
On July 11, 2023, Unit 42 cloud researchers discovered a new peer-to-peer (P2P) worm they dubbed P2PInfect. Written in the highly scalable and cloud-friendly Rust programming language, this worm is capable of infecting across platforms. It targets Redis, a popular open-source database application widely used in cloud environments.
P2PInfect - a self-replicating peer-to-peer worm
Redis instances can run on both Linux and Windows operating systems. Unit 42 researchers have identified over 307.000 Redis systems that have communicated publicly in the last two weeks, of which 934 may be vulnerable to this P2P worm variant. Even if not all of the 307.000 Redis instances are vulnerable, the worm will still attack those systems and attempt to compromise them.
The P2PInfect worm infects vulnerable Redis instances by exploiting the Lua sandbox escape vulnerability (CVE-2022-0543). This makes the P2PInfect worm more effective for operating and spreading in cloud container environments. Here, Unit 42 researchers discovered the worm by compromising a Redis container instance in their HoneyCloud environment.
Worm attacks Redis container in honey pot
This is a set of honeypots designed to identify and investigate novel cloud-based attacks in public cloud environments. Although the vulnerability was announced in 2022, its scope is not yet fully known. However, it is rated with a critical CVSS score of 10,0 in the NIST National Vulnerability Database. Also, the fact that P2PInfect exploits Redis servers running on both Linux and Windows operating systems makes it more scalable and effective than other worms. The P2P worm observed by the researchers serves as an example of a serious attack that would be possible using this vulnerability.
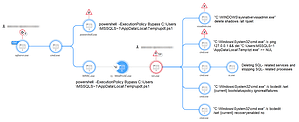
Mallox Ransomware: Significant increase in activity
Mallox, also known as TargetCompany, Fargo and Tohnichi, is a ransomware strain that targets Microsoft (MS) Windows systems. Active since June 2021, it is characterized by exploiting insecure MS-SQL servers as a penetration vector to compromise victims' networks.
Recently, Unit 42 researchers have observed an increase in Mallox ransomware activity. Since the beginning of 2023, Mallox activities have steadily increased. According to telemetry and open source data, the number of Mallox attacks increased by 2023 percent in 2022 compared to 174. The Mallox ransomware group claims hundreds of victims. While the actual number of victims is unknown, Unit 42 telemetry data suggests dozens of potential victims worldwide, spread across various industries including manufacturing, professional and legal services, wholesale and retail.
Mallox uses double blackmail
Like many other ransomware groups, Mallox ransomware follows the double ransom trend: the attackers steal data, encrypt the files, and threaten to publish the stolen data on a leaking website in order to get victims to pay the ransom. Each victim receives a private key to communicate with the group via Tor browser and negotiate terms and payment.
Researchers recommend using an XDR/EDR solution to perform in-memory inspection and detect process injection techniques. Threat hunting allows organizations to look for signs of unusual behavior related to security product bypass, lateral movement service accounts, and user behavior related to domain administrators.
More at PaloAltoNetworks.com
About Palo Alto Networks Palo Alto Networks, the global leader in cybersecurity solutions, is shaping the cloud-based future with technologies that transform the way people and businesses work. Our mission is to be the preferred cybersecurity partner and protect our digital way of life. We help you address the world's biggest security challenges with continuous innovation leveraging the latest breakthroughs in artificial intelligence, analytics, automation, and orchestration. By delivering an integrated platform and empowering a growing ecosystem of partners, we are the leaders in protecting tens of thousands of businesses across clouds, networks and mobile devices. Our vision is a world where every day is safer than the one before.