New InterPlanetary Storm malware variant targets IoT devices. The infected devices open back doors for cryptomining, DDoS and other large-scale attacks.
The cybercriminal organization behind the InterPlanetary Storm malware has released a new variant that, in addition to Windows and Linux computers, now also targets Mac and Android devices. The malware is building a botnet that currently includes around 13.500 infected computers in 84 different countries around the world, and that number continues to grow.
After Windows and Linux now IoT devices
The first variant of InterPlanetary Storm, which targeted Windows machines, was revealed in May 2019, and in June of this year a variant was reported that is capable of attacking Linux machines. The new variant, which Barracuda researchers discovered for the first time at the end of August, targets IoT devices such as televisions that run on Android operating systems, as well as Linux-based machines such as routers with poorly configured SSH service. The botnet that this malware sets up does not yet have any clear functionality, but offers the campaign operators a back door into the infected devices so that they can later be misused for cryptomining, DDoS or other large-scale attacks.
The majority of the computers infected by the malware are currently located in Asia.
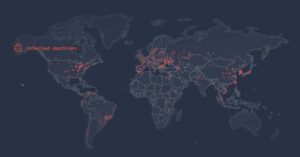
• 59% of infected computers are in Hong Kong, South Korea, and Taiwan.
• 8% in Russia and Ukraine
• 6% in Brazil
• 5% in the United States and Canada
• 3% in Sweden
• 3% in China
• All other countries register 1% or less (Germany currently 0,5%)
How the new InterPlanetary Storm malware works
The new variant of the InterPlanetary Storm malware gains access to computers by carrying out a dictionary attack on SSH servers, similar to FritzFrog, another peer-to-peer (P2P) malware. It can also gain access by accessing open ADB servers (Android Debug Bridge). The malware detects the CPU architecture and operating system of its victims, and it can run on ARM-based machines, an architecture that routers and other IoT devices use quite often. The malware is known as InterPlanetary Storm because it uses the InterPlanetary File System (IPFS) p2p network and the underlying libp2p implementation. This allows infected nodes to communicate with one another directly or via other nodes (e.g. relays).
Special properties of the new variant
This variant of InterPlanetary Storm is written in Go, uses the Go implementation of libp2p and is packed with UPX. It spreads using SSH brute force and open ADB ports, and exposes malware files to other nodes on the network. The malware also enables reverse shell and can run bash shell. The new variant has several unique features designed to help ensure that malware remains persistent and protected after it has infected a computer:
- It recognizes honeypots. The malware looks for the string "svr04" in the standard shell prompt (PS1), which was previously used by the Cowrie honeypot.
- It updates itself automatically. The malware compares the version of the running instance with the latest available version and updates itself accordingly.
- It tries to stay persistent by installing a service (system / systemv) using a Go Daemon Package.
- It stops other processes on the computer that pose a threat to the malware, such as debuggers and competing malware.
Measures to protect against new InterPlanetary Storm variant
- Properly configured SSH access on all devices: This means that keys are used instead of passwords, which makes access more secure. If the password login is activated and the service itself is accessible, the malware can exploit the poorly configured attack surface. This is a problem for many routers and IoT devices, making them easy targets for this malware.
- Using a Cloud Security Posture Management Tool to monitor SSH access control to avoid any configuration errors that could have serious consequences. If necessary, secure access to shells should be provided; Instead of exposing the resource on the Internet to threats, an MFA-enabled VPN connection should be provided and the networks segmented for the specific requirements, instead of granting access to wide IP networks.
More on this on the blog at Barracuda.com
[starboxid=5]
