The SophosLabs have uncovered a new hacking strategy. Apparently confused attack methods should let security mechanisms run nowhere. But the forensic experts at SophosLabs are on to them and have recently unmasked a new method of attack.
A new attack method has hit the net for the specialists at SophosLabs. Security experts Fraser Howard and Andrew O'Donnell came across an unusual variant in their hunt for new threats. In summary, the chain of attacks begins with a malicious email message including VB scripting code and ends with the placement of a remote access Trojan called MoDi RAT. During their forensic examinations, however, the specialists discovered some surprising actions in the confused sequence of attacks. This included, for example, starting a Visual Basic script file, which in turn activates a PowerShell in order to literally paste the text of the commands into the PowerShell window via the clipboard instead of passing the command string as a parameter. The goal behind it: Fileless attack scripts should avoid detection by security mechanisms in connection with the clipboard. This is exactly what all security experts are looking for in order to prepare protective solutions for such attacks.
Hacker strategy relies on tricks
“In our investigations, we uncovered some interesting telemetry data that indicate cybercriminals are attempting to evade detection. This is a general trend that we are seeing particularly this year. Attackers try different methods to improve their chances. The latest telemetry data was reason enough to delve deeper. In doing so, we uncovered some interesting tricks - notably the use of VBScript to inject the malicious commands into the PowerShell process. The goal of this approach was, with a high degree of certainty, to evade detection and stay out of sight of security teams,” said Fraser Howard, threat research director at Sophos.
Attack in confused steps - this is how it works
The entire attack chain sounds confused and not necessarily logical. But cyber criminals use just such tricks to try to prevent detection using security mechanisms. The individual steps remain under the radar and attract no attention.
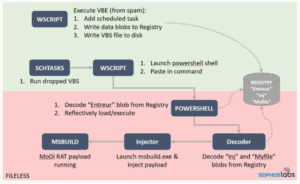
The attack begins when the spam email is opened. The attached Visual Basic script connects to a remote location, the entry point into a series of HTTP 302 redirects. These in turn lead to a zip archive that is hosted on OneDrive cloud storage and contains an encoded VBS file.
In the next phase, the first VBScript writes a second VBS file into the file system and adds three new entries with binary data to the Windows registry, which are output as 8-digit binary numbers. The system service is then started to create a new scheduled task. This should start the VBS script at a previously defined future time.
When this scheduled task runs, it uses wscript.exe to start the VBS. The VBS code in turn starts PowerShell and executes a code that takes data from the VBS and places it on the clipboard. These data or commands are then inserted into the PowerShell window under program control using the VBS SendKeys command.
In the subsequent steps, PowerShell extracts a .NET decoder execution file from one of the registry blobs (called Entreur) that the VBE had previously created and loads it reflective by injecting it into a system process. The executable decoder file then extracts the .NET injector and the payload blobs (called inj or Myfile in the registry) from the registry. Finally, the injector loads the payload (injects into the host application msbuild.exe). The procedure for this attack is a little easier to understand in the diagram.
What can a company do?
It is extremely important that no older Windows operating systems are used in the IT infrastructure. The reason lies in the AMSI framework from Microsoft. This is only available in newer versions of Windows (Windows 10, Windows Server 2016 and Windows Server 2019) and provides the basis for detecting and repelling such attacks. Cyber criminals know that even older systems are in use and make intensive use of this security gap.
More on this at Sophos.com[starboxid=15]