
Aqua Security launches new 2022 Cloud Native Threat Report. Cryptomining malware is still the number one, but backdoors and worms already account for more than half of all attacks. Attackers are increasingly targeting Kubernetes and the software supply chain.
Aqua Security, the leader in cloud native security, has released its 2022 Cloud Native Threat Report: Tracking Software Supply Chain and Kubernetes Attacks and Techniques study. The study was prepared by Team Nautilus, Aqua Security's research unit specializing in cloud native technology, and aims to provide insights into trends and key insights for practitioners about the cloud native threat landscape.
Among other things, the investigation revealed that attackers are increasingly using new tactics, techniques and processes to specifically target cloud-native environments. Attackers are also increasingly using multiple attack components and are increasingly turning their attention to Kubernetes and the software supply chain.
More than cryptomining in mind
While cryptominers were still the most frequently observed malware, Team Nautilus discovered an increased use of backdoors, rootkits and credential stealers with increasing frequency. These are signs that intruders have more than cryptomining on their minds. Backdoors, which allow a threat actor to remotely access a system and remain in the compromised environment, were found in 54 percent of attacks. That was 9 percent more than the same 2020 survey. Additionally, half of the malicious container images analyzed by the researchers (51 percent) contained worms, allowing attackers to scale up the scope of their attack with minimal effort.
Here, too, a significant increase of 10 percent compared to 2020 was recorded. Notably, threat actors have also expanded their targets to CI/CD and Kubernetes environments. In 2021, 19 percent of malicious container images analyzed targeted Kubernetes, including kubelets and API servers, a 9 percent increase from the previous year.
Other important results of the study
- The proportion and variety of observed attacks on Kubernetes has increased, which includes broader adoption of the arming of Kubernetes UI tools.
- Supply chain attacks make up 14 percent of the specific sample of images from public image libraries. This shows that these attacks continue to be an effective method for attacking cloud-native environments.
- The Log4j zero-day vulnerability was immediately exploited in the wild. Team Nautilus discovered several malicious techniques including known malware, fileless execution, reverse shell executions, and files downloaded from memory and executed. This highlights the need for runtime protection.
- Researchers observed TeamTNT honeypot attacks even after the group announced its retirement in December 2021. However, no new tactics were used, so it is unclear whether the group is still active or whether the ongoing attacks originated from an automated attack infrastructure. Regardless, business teams should continue to take preventive measures against these threats.
Container sandbox solution DTA is used
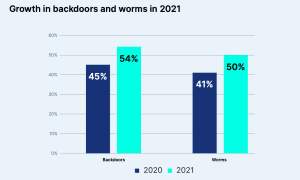
🔎 Backdoors and worms are on the rise - the attackers have more in mind than cryptomining (Image: Aqua Security)
Aqua's team Nautilus used honeypots to research attacks in the wild. To analyze supply chain attacks on cloud-native applications, the team examined images and packages from public registries and repositories, such as DockerHub, NPM, and the Python Package Index. Team Nautilus used Aqua's Dynamic Threat Analysis (DTA) product to analyze each attack. Aqua DTA is the industry's first container sandbox solution that dynamically evaluates the behavior of container images to determine if they harbor hidden malware. This allows organizations to identify and mitigate attacks that static malware scanners cannot detect.
"The results of this study underscore the fact that cloud-native environments are now a target for attackers and that techniques are constantly evolving," said Assaf Morag, Threat Intelligence and Data Analyst Lead at Aqua's Team Nautilus. “The broad attack surface of a Kubernetes cluster is attractive to threat actors, and once inside, they look for easy targets to attack.
The key takeaway from this report is that attackers are more active than ever, targeting vulnerabilities in application, open source, and cloud technology with increasing frequency. Security professionals, developers, and DevOps teams need to look for security solutions that are purpose-built for cloud-native. Implementing proactive and preventive security measures enables stronger security and ultimately protects complete environments.”
To ensure the security of cloud environments, Aqua's team at Nautilus recommends implementing runtime security measures, a layered approach to Kubernetes security, and scanning in development. Aqua Security's 2022 Cloud Native Threat Report is available for free download.
More at AquaSec.com
About Aqua Security Aqua Security is the largest pure cloud native security provider. Aqua gives its customers the freedom to innovate and accelerate their digital transformation. The Aqua platform provides prevention, detection, and response automation across the application lifecycle to secure the supply chain, cloud infrastructure, and ongoing workloads—regardless of where they are deployed.
