
With the analysis of metadata instead of the usual Deep Packet Inspection (DPI), the Swiss cybersecurity company Exeon Analytics is establishing a modernized and future-proof Network Detection & Response (NDR) solution in the European market.
In contrast to the established methods based on DPI, the metadata analysis is not affected by encrypted data traffic. This is relevant as modern cyber attacks such as APTs, ransomware and lateral movements rely heavily on encrypted communication for attack instructions from remote command and control servers (C&C).
Encrypted metadata stands out
Traditional NDR solutions typically detect such events using comprehensive data analysis, which cannot be done in the case of encrypted data traffic. Exeon's technology is based on metadata that is fully available even in the case of encrypted data traffic.
"While the DPI approach provides detailed analysis of individual data packets, it requires an immense amount of processing power and is blind to encrypted network traffic," said Gregor Erismann, CCO of Exeon Analytics. “Metadata analysis allows to overcome these limitations. By analyzing metadata, network communication can be observed at any point of collection and enriched with information that provides insight into the encrypted communication.”
Monitor encrypted traffic
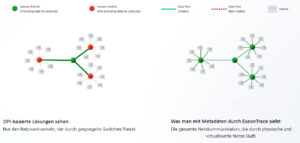
🔎 Graphic comparison: What do DPI-based solutions see and what you see with metadata in ExeonTrace. (Image Exeon).
With the ExeonTrace NDR solution, security teams can monitor all communication, including encrypted data traffic, even in complex and distributed IT/OT networks with very high bandwidth. To provide security teams with information about all network traffic, metadata analysis captures a variety of attributes about network communications, applications and actors. For example, the source/destination IP addresses, the session duration, the protocols used (TCP, UDP) and the type of services used are recorded.
In addition, by analyzing log data, many other important attributes can be collected, which are effective in detecting and preventing advanced cyber attacks. This includes, for example, DNS and DHCP information, the assignment of users to systems based on DC log data or various object hashes of JavaScripts and images.
Efficient storage and facilitated forensics
The analysis of metadata, supplemented by system and application logs, enables security teams to identify network vulnerabilities (e.g. shadow IT) and cyber threats at an early stage, as well as to sharpen visibility into the entire IT/OT network. In addition, lightweight metadata allows for efficient storage of historical records, greatly facilitating forensic investigations. In addition, the use of an NDR solution based on the metadata approach makes it possible to monitor all data traffic in the corporate network in order to identify suspicious activities and vulnerabilities on all devices connected to the network - including IoT devices.
More at Exeon.com
About Exeon Analytics
The Swiss cybertech company specializing in protecting IT and OT infrastructures through AI-driven security analytics. The Network Detection & Response (NDR) platform ExeonTrace offers companies the opportunity to monitor networks, immediately detect cyber threats and thus effectively protect their own company's IT landscape - quickly, reliably and completely hardware-free.
