The high number of attacks in which compromised login data are misused shows that passwords alone are no longer sufficient as a trustworthy identification of legitimate users, but that the use of multi-factor authentication (MFA) has become a fundamental building block for corporate security.
MFA requires users to provide convincing proof of their identity in addition to their login credentials. According to Microsoft, MFA can prevent identity-based attacks based on stolen credentials up to 99,9 percent. Even if a user's credentials are compromised, MFA attackers make it extremely difficult to circumvent the authentication requirements.
How does multi-factor authentication work?
MFA adds further steps to the authentication process. The number of these steps varies depending on the configuration and context. The three basic MFA categories are:
1. Something you know
The simplest example of this category is a password or any variation of memorable data that is set up by or for the user. This category includes personal background questions that probably only the user can answer. This category is generally considered to be the least secure, as both passwords and private information can be compromised or guessed by attackers.
2. Something you own
This category is much more difficult to compromise. It comprises various physical units that only the user has - for example cell phones, physical tokens, key fobs or smart cards. The physical entity can either serve as the carrier of the verification step - for example a mobile phone that displays a one-time password - or it can itself be the object of authentication, such as a physical token. The latter is considered more secure, as less data is exchanged during authentication, so that an attacker cannot intercept it so easily.
3. Something that you are
This is considered to be the most secure category of factors and includes physical identifiers. The most common use is a fingerprint on a mobile phone or on a hardware token, but voice, facial recognition and other unique biometric features are also used. Any combination of these three categories of authentication factor significantly increases security and reduces the likelihood of the account being compromised.
Examples of traditional MFA solutions
In corporate environments, MFA is often used in conjunction with a Single Sign On (SSO) solution to increase the security of the individual password used by the workforce.
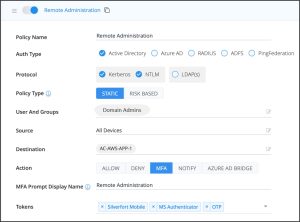
Static vs. risk-based MFA
With a static MFA, every time a user tries to access a resource, an MFA is required. This can be cumbersome and disrupt operational processes. To avoid such disruptions and to keep MFA in line with business needs, many organizations choose either or both of the following:
Static MFA is only applied to users when they are accessing sensitive resources. This can still be very cumbersome and disruptive for administrators who work with many sensitive resources on a daily basis.
With a risk-based approach, MFA is only required if the level of risk is high. This is known as adaptive authentication or risk-based authentication (RBA). A risk engine is used that evaluates various factors. It only requires additional verification factors if the level of risk suggests that the credentials provided may have been compromised.
MFA everywhere: Agentless multi-factor authentication
For a holistic protection of identities, Unified Identity Protection solutions make it possible to enforce MFA on all resources - even on those that could not previously be covered, both in on-prem and in multi-cloud environments, and without agents or proxies.
To achieve this, the traditional MFA architecture is fundamentally changed. Instead of relying on the agents on the devices, a Unified Identity Protection solution communicates directly with the Identity and Access Management (IAM) solution itself, monitors the authentication protocols and enforces MFA based on them. Whenever a user tries to access a resource, he authenticates himself with an IAM solution (for example Active Directory, Okta, Ping Azure AD, etc.). After authentication on the IAM solution, the access request is forwarded to the Unified Identity Protection platform.
Platform analysis for every access request
The platform then analyzes the context of every access request from a user or service account using an AI-controlled risk engine. Then it applies the appropriate access policy. If the risk is high, the solution can increase authentication requirements and ask the user for multi-factor authentication. If the MFA task was completed correctly, the Unified Identity Protection solution instructs the IAM to grant the user access to the resource. If the MFA task has not been solved or the access guidelines require it, access can be completely blocked.
This novel architecture enables MFA to be extended to practically any resource that authenticates itself to the IAM solution in the company's environment, as well as to any access interface. As long as the resource that a user wants to access is authenticated at the IAM, it is also subject to MFA through the Unified Identity Protection platform. This enables real-time prevention of common attack scenarios such as automated ransomware distribution and on-premises lateral movement.
Cloud without multi-factor authentication is dangerous
The development of the IT landscape makes secure authentication more important than ever today. Before the cloud era, attackers had to bypass perimeter protection mechanisms in order to gain a foothold on the network and install malware on an endpoint or server. Today, due to the gradual transition to the cloud, large amounts of sensitive business data are stored on the public Internet. Without the added protection of MFA, this data is just one password away from cybercriminals.
More at Silverfort.com
About Silverfort Silverfort is the provider of the first Unified Identity Protection Platform that consolidates IAM security controls in corporate networks and cloud environments in order to ward off identity-based attacks. Through the use of innovative agent-free and proxy-free technology, Silverfort integrates seamlessly into all IAM solutions, standardizes their risk analysis and security controls and extends their coverage to assets that previously could not be protected, such as self-developed and legacy applications, IT infrastructure , File systems, command-line tools, machine-to-machine access and more.