
Many authorities and companies use Microsoft products, the Microsoft Office product range with teams in particular is very popular, also in the cloud version. As Proofpoint's security experts have shown in the past, this cloud migration brings new cyber risks, such as phishing, stolen logins and identities.
Attackers are currently increasingly targeting cloud environments and services and trying to exploit existing security gaps and vulnerabilities for their own purposes. In recent months and years, cybercriminals have used Microsoft services for attacks and, for example, effectively used Microsoft Sway as a weapon, bypassing security measures.
Many Microsoft applications are under attack
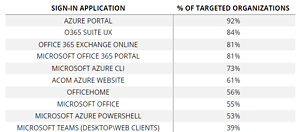
🔎 The ten most attacked login applications from Microsoft in the second half of 2022 (Image: Proofpoint).
Sway is far from the only Microsoft application being abused by cybercriminals. Proofpoint security researchers recently analyzed over 450 million attacks targeting Microsoft 2022 cloud tenants in the second half of 365. According to the analysis results, Microsoft Teams is among the ten most frequently attacked applications. Almost 40 percent of the organizations attacked had at least one unauthorized login attempt.
Reason enough for Proofpoint to take a closer look at the Microsoft application Teams. During their investigation, the experts uncovered multiple Microsoft Teams abuse methods, which cybercriminals effectively use to phish M365 credentials, distribute dangerous executables and propagate their access in a compromised cloud environment. These tactics include:
- Post-account compromise impersonation and manipulation techniques, including the use of tabs to phish or distribute malware.
- Abusing meeting invitations by replacing standard URLs with malicious links.
- Abusing messages by replacing existing URLs with malicious links.
The attack methods examined by Proofpoint require access to a compromised user account or a teams token. By 2022, around 60 percent of M365 subscribers will have at least one successful account takeover. As a result, there is significant potential for attackers based on Teams capabilities to move laterally into victim systems following a compromise.
M365 subscribers: accounts cracked at 60 percent
Analysis of past attacks and current trends within the cloud threat landscape also shows that attackers are increasingly adopting more advanced attack methods. The use of new attack techniques and tools combined with apparent security flaws, including dangerous features in third-party applications, exposes organizations to a variety of major risks.
In addition, cybercriminals are constantly looking for new ways to steal user credentials and gain access to user accounts. As Proofpoint's latest research illustrates, Microsoft Teams can be used as a platform for various forms of cloud attacks as it is a legitimate and popular cloud application.
The Proofpoint experts have published the complete investigation in a blog, in which the attack methods are explained in detail using screenshots.
More at Proofpoint.com
About Proofpoint Proofpoint, Inc. is a leading cybersecurity company. The focus for Proofpoint is the protection of employees. Because these mean the greatest capital for a company, but also the greatest risk. With an integrated suite of cloud-based cybersecurity solutions, Proofpoint helps organizations around the world stop targeted threats, protect their data, and educate enterprise IT users about the risks of cyberattacks.
