McAfee has released its new Quarterly Threats Report. For the April issue, McAfee Labs examined the malware activity of cyber criminals and the evolution of cyber threats in the third and fourth quarters of 2020.
On average, McAfee researchers registered 4 threats per minute in the fourth quarter - an increase of 648 threats per minute (60 percent) from Q10. Donoff malware activity also continued to grow, increasing PowerShell threats by 3 percent.
All threats are increasing
The volume of registered attacks already rose in Q3 to Q4 2020 to an average of 588 processes per minute (Image: McAfee).
In addition, Covid-19 remains popular with attackers: While the pandemic continued to spread worldwide, cyber criminals were already busy attacking workforces who were in unprecedented numbers in the home office with the restrictions of the pandemic, the potential weak points of their remote devices and the security of their bandwidth struggled. In the second quarter, McAfee recorded an increase of 605 percent in attacks of this type. In the third quarter this value rose again by 240 percent and in the fourth by a further 114 percent.
“The world and companies have now adapted to the pandemic-related restrictions as well as the challenges that entire workforces in the home office pose. And it did so as security threats became more complex and prevalent, ”said Raj Samani, McAfee Fellow and Chief Scientist. “The employees can now do their work more routinely and efficiently within their own four walls, while the companies increasingly had to defend themselves against opportunistic attackers who have added the Covid-19 issue to their repertoire of attacks. In addition, ransomware and malware attacks target vulnerabilities in applications and processes used in companies. This allows cyber criminals to take over networks and data, causing millions in damage to assets and recovery costs. "
Malware attacks remain a constant threat
In the third quarter of 2020, McAfee researchers observed an average of 588 threats per minute, an increase of 169 threats per minute (40 percent) compared to the previous quarter. In the fourth quarter, that average rose to 648 threats per minute, up from 60 threats per minute, or 10 percent. The results in detail:
- PowerShell threats: Grew 4 percent in Q208, primarily from Donoff malware. McAfee identified numerous PowerShell attacks that use process injection to inject code into legitimate processes as a privilege escalation technique.
- Mobile malware: Increased 4 percent in Q118, partly due to an increase in SMS reg samples. HiddenAds, Clicker, MoqHao, HiddenApp, Dropper and FakeApp were the most popular variants.
- Attacks with ransomware: Increased 3 percent from Q4 to Q69 and was driven by Cryptodefense. The groups REvil, Thanos, Ryuk, RansomeXX and Maze topped the list of ransomware families.
- MacOS malware: Exploded 3 percent in Q420 due to EvilQuest ransomware, but then slowed down towards the end of last year.
Publicly Reported Incidents: McAfee saw publicly reported incidents in the technology sector increase 2020 percent in the fourth quarter of 100. In the public sector, the number rose by 93 percent over the same period.
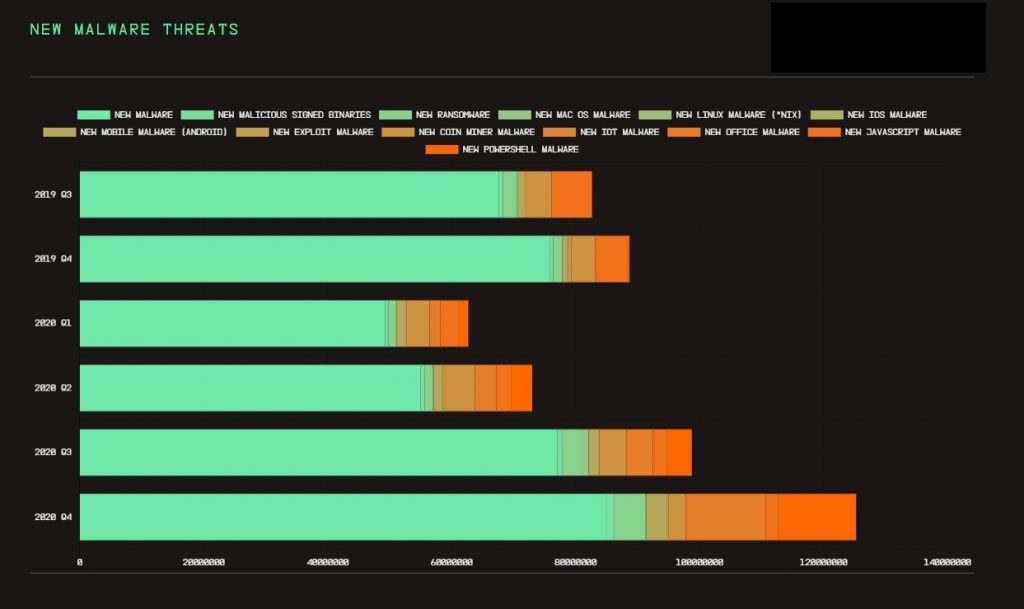
The bar chart shows the massive growth the evaluated Q4 has compared to the other quarters (Image: McAfee).
Affected, attack vectors and vulnerabilities
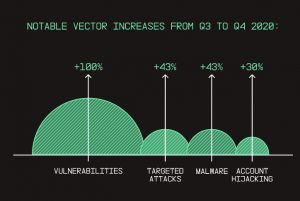
Attack vectors: Malware was the top-reported cause of security incidents in the fourth quarter, followed by account hijacking, targeted attacks, and vulnerabilities. Incidents related to new vulnerabilities increased 4 percent in Q100, malware and targeted attacks increased 43 percent each, and account hijacking increased 30 percent.
Exploited vulnerabilities: Among the campaigns that McAfee monitored and investigated, the Enternal Blue exploit was the most prominent in the fourth quarter of 2020.
Attackers still focus on cloud users
McAfee researchers found nearly 3,1 million external attacks on cloud user accounts. This value is based on the analysis of anonymized cloud data from more than 30 million McAfee MVISION cloud users worldwide in the fourth quarter of 2020. This data set contains information on the most important industrial sectors in the world: including finance, healthcare, public sector, technology, manufacturing Commercial, retail, transportation and business services.
Cyber criminals rely on various MITER ATT & CK techniques
The most common MITER ATT & CK techniques that McAfee registered in QXNUMX and QXNUMX included System Information Discovery, Obfuscated Files or Information, File and Directory Discovery, Data Encryption for Impact, Stop Services, Process Injection, Process Discovery, Masquerading Techniques, and Exploits of Public Facing Applications.
System information discovery
Was one of the more noticeable MITER techniques in the campaigns McAfee investigated in the fourth quarter of 2020. The malware included functions in these campaigns that allowed it to collect the operating system version, hardware configuration and host name from a victim's computer and report it back to the attacker.
Obfuscated Files or Information
The second most frequently observed technique during this period. A notable example was the use of virtual hard drive (VHD) files by the APT28 group to package and disguise their malware to defeat security technologies.
Process injection
This privilege escalation technique has been observed by McAfee on several malware families and threat groups including PowerShell threats, RAT tools such as Remcos, ransomware groups such as REvil, and several government sponsored APT groups.
More at McAfee.com
About McAfee McAfee Corp. (Nasdaq: MCFE) is one of the world's leading cyber security companies, with solutions from the end device to the cloud. Inspired by the strength of close collaboration, McAfee develops solutions to create a safer world for business and private customers.
