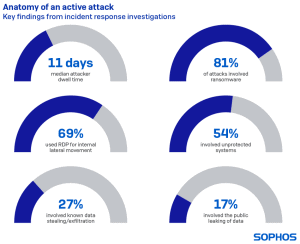
New Sophos Incident Response Almanac: Cyber gangsters stay undetected in networks for an average of 11 days. Sophos publishes new "Active Adversary Playbook 2021" with telemetry data from its MTR and Rapid Response team: Hackers used more than 400 different tools and techniques, 81 percent of the incidents involved ransomware and 69 percent of the attacks involved remote Desktop Protocol (RDP) used for crawling.
Sophos has published its “Active Adversary Playbook 2021”. It describes the attackers' behavior, tools, techniques, and procedures (TTPs) as they were observed by Sophos threat hunters and analysts from 2020 through spring 2021. The playbook is based on telemetry data and 81 investigations of specific incidents by the Sophos Managed Threat Response (MTR) team and the Sophos Rapid Response team. The aim of the new almanac is to support security teams in better understanding attack tactics and in identifying and defending against malicious activities in networks more effectively.
The results show, among other things, that the attackers stayed on the network for an average of eleven days before they were discovered, with the longest undetected intrusion even lasting 15 months. Ransomware was involved in 81 percent of the incidents and 69 percent of the attacks used the remote desktop protocol (RDP) to infiltrate the network laterally.
The main findings of the report
The attackers' average length of stay before discovery was 11 days
To put this into context, eleven days offer attackers a potential 264 hours for criminal activities such as access data theft or data exfiltration. Considering that some of these activities take minutes or hours to complete, 11 days is infinite time to wreak havoc on a company's network. Exception: Attacks with traditional ransomware usually showed a shorter dwell time, as this is only about destruction.
The Remote Desktop Protocol (RDP) played a role in 90% of the attacks examined
In addition, the attackers used RDP in 69 percent of all cases for undetected movement in the network. Security measures for RDP such as VPNs or multifactor authentication usually focus on protecting external access. However, they will not work if the attacker is already inside the network. As a result, attackers are increasingly using RDP to infiltrate a system in active, keyboard-controlled attacks, e.g. with ransomware.
Interesting relationships can be found among the five most frequently used tools
For example, when PowerShell is used in an attack, Cobalt Strike is involved 58 percent of the time, PsExec 49 percent, Mimikatz 33 percent, and GMER 19 percent. Cobalt Strike and PsExec are used together in 27 percent of the attacks, while Mimikatz and PsExec are used together in 31 percent of the attacks. After all, the combination of Cobalt Strike, PowerShell and PsExec occurs in 12 percent of all attacks. Such correlations are important because their detection can serve as an early warning of an impending attack or confirm the presence of an active attack.
Ransomware was involved in 81 percent of the attacks that Sophos investigated
The actual ransomware activation is often the first time an attack becomes visible to an IT security team. Unsurprisingly, the vast majority of incidents documented by Sophos involved ransomware. Other types of attacks included pure data exfiltration, cryptominer, banking Trojans and pen test attacks.
It is not always easy to distinguish between good and bad
“The threat landscape is becoming increasingly confusing and complex. Cyber criminals launch their attacks with a wide variety of skills and resources, from script kiddies to government-sponsored hacking groups. That makes it difficult for defenders to work, ”said John Shier, senior security advisor at Sophos. "Over the past year, our incident response team has helped neutralize attacks that were carried out by various attack groups using more than 400 different tools."
Many of these tools are also used by IT administrators and security professionals for their daily tasks, and it is a challenge to identify the difference between benign and malicious activities in a timely manner. Given that attackers spend an average of eleven days on the network while interfering with routine IT activities, Shier says it is important that defenders know the warning signs to watch out for and investigate. For example, a red alert should be raised if a legitimate tool or known activity is discovered in an unexpected place or at an extraordinary time. Shier continues: "Technology can make a big difference these days, but in the current threat landscape, human experience and the ability to respond individually are an important part of any security solution."
Further topics in the “Active Advisary Playbook 2021” are the most frequently used attack techniques and tactics, the earliest signs of an attack, the most observed threat types and the most frequently identified groups of hackers.
More at Sophos.com
About Sophos More than 100 million users in 150 countries trust Sophos. We offer the best protection against complex IT threats and data loss. Our comprehensive security solutions are easy to deploy, use and manage. They offer the lowest total cost of ownership in the industry. Sophos offers award-winning encryption solutions, security solutions for endpoints, networks, mobile devices, email and the web. In addition, there is support from SophosLabs, our worldwide network of our own analysis centers. The Sophos headquarters are in Boston, USA and Oxford, UK.