
Even if the feared mass exploitation of the Log4j / Log4Shell vulnerability has not yet taken place, the bug will be a target for attacks for years to come, according to Chester Wisniewski, Principal Research Scientist at Sophos. So far there has been no big Log4j / Log4Shell earthquake - a forensic status finding.
Sophos' expert teams have forensically analyzed the events surrounding the Log4Shell vulnerability since its discovery in December 2021 and first balance pulled - including a future forecast by Principal Research Scientist Chester Wisniewski and various graphics showing the exploitation of the vulnerability. The summary: The big crisis due to mass exploitation by cybercriminals has not materialized so far, although this was feared across the industry. However, the absence of the expected and devastating effects does not mean the all-clear. Because the Log4Shell bug, which is deeply hidden in many digital applications and products, can probably be a target for cybercriminals for years to come.
Acting quickly prevented the worst
The Sophos experts are of the opinion that the direct and mass attacks on the Log4Shell vulnerability have so far been successfully contained, above all through the active action of all those involved. The scope of the vulnerability has successfully united the digital and security community. Collaborative action is not new, it was already the case with the Y2000K bug in 2 and it seems to have made a big difference here too. The moment the details of the Log4j vulnerability emerged, the world's largest and most important cloud services, software vendors, and corporations took action to stay off the iceberg and prevent a catastrophe. This was also made possible by the collective intelligence and practical guidance of the security community.
Limited mass dispersal
The Sophos Managed Threat Response Team (MTR) found that while many scans and attempts to exploit the Log4Shell exploit were detected, few MTR customers had actually encountered intrusion attempts via Log2022j as of early January 4. One explanation for this could be the need to adapt the attack to each application that contains the vulnerable Apache Log4J code.
Therefore, the widely used applications that contain the vulnerability are exploited in an automated manner to a greater extent than others. An example of this is VMware Horizon - this is where the first breach observed by Sophos MTR via the Log4Shell vulnerability took place.
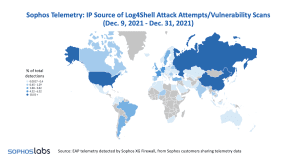
The heavy weighting of the US and Germany in the IP source data probably reflects the large data centers (Image: Sophos).
Significant shifts in geo-telemetry
Sophos Geo telemetry since the vulnerability was discovered through the first two weeks of January 2022 shows interesting variations in the sources of attack attempts and scans. The December 2021 map makes it clear that regions such as the US, Russia, China, Western Europe and Latin America are more affected. The heavy weighting of the US and Germany in the geographic IP source data likely reflects the large data centers located there, such as Amazon, Microsoft, and Google.
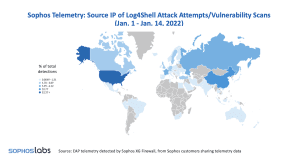
The situation picture at Log4j and the number of detected incidents will change dramatically in early 2022 (Image: Sophos).
The Log4j situational picture and the number of incidents detected will change dramatically in early 2022 (Image: Sophos). This situational picture and the number of incidents identified will change dramatically in early 2022. The most striking difference is that the initial dominance of Russia and China seems to have diminished in January. According to Sophos findings, this reflects an apparent decrease in attack attempts by a small number of highly aggressive cryptanalysts in these regions.
A conclusion from Sophos
Sophos' teams of experts believe that attempts to exploit the Log4Shell vulnerability will likely continue for years to come and will be a popular target for penetration testers and for nation states and their threat actors. The urgency of finding out where the vulnerability might be occurring in one's own network and patching appropriate applications therefore remains the most important goal.
More at Sophos.com
About Sophos More than 100 million users in 150 countries trust Sophos. We offer the best protection against complex IT threats and data loss. Our comprehensive security solutions are easy to deploy, use and manage. They offer the lowest total cost of ownership in the industry. Sophos offers award-winning encryption solutions, security solutions for endpoints, networks, mobile devices, email and the web. In addition, there is support from SophosLabs, our worldwide network of our own analysis centers. The Sophos headquarters are in Boston, USA and Oxford, UK.
