
The 2022 OT Cybersecurity Survey Report shows the significant increase in cyber risks against the background of large-scale OT attacks. In response, organizations are increasing their security budgets for OT security. American and European companies were surveyed.
Otorio, a provider of next-generation OT cyber and digital risk management solutions, reveals the current state of OT security in its 2022 OT Cybersecurity Survey Report. 98 percent of those surveyed reported an increase in cyber risks over the past three years. 67 percent of those surveyed said risks had increased significantly, and 31 percent responded that there had been a slight increase. These results are not surprising given last year's headlines about spectacular OT cyberattacks. Worldwide attacks by Lockbit ransomware, the attack on Colonial Pipeline in the USA or attacks on mineral oil sales in Europe are just a few of the most prominent examples.
Cyber security incidents: not all reported
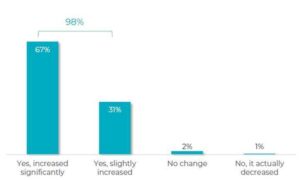
🔎 In the survey, 98 percent state that cyber risks have increased, in some cases sharply, in recent years (Image: Otorio).
When asked what percentage of companies had reported cybersecurity incidents to government agencies in the past 58 months (at the time of the survey), all companies indicated that they generally do so. In day-to-day operations, however, 20 percent do not report at least XNUMX percent of their incidents, while only four percent actually report all of their incidents in full. This means that the incidents that make the headlines represent only a fraction of the true scale of OT cyberattacks in the industry.
The key areas of OT security this year
The top areas OT cybersecurity is currently focusing on are improving visibility and asset inventory (39 percent), detection capabilities (23 percent), and responsiveness (20 percent). Many companies focus on optimizing what already exists.
However, it is also worth considering whether perhaps a new approach would solve more of their challenges. One way to do this is to proactively identify and mitigate risks before they become security incidents. Moving from an Indication of Compromise (IoC) to an Indication of Exposure (IoE) approach makes OT security simpler and much more efficient.
99 percent of companies want to increase OT cybersecurity budgets
99 percent of organizations said they will increase their OT cybersecurity budgets this year, with more than half (54 percent) planning an increase of more than 50 percent. 92 percent will increase it by at least 10 percent. This is understandable given a significant increase in cybercrime, more regulation than ever, digital transformation and the shift to connected manufacturing. OT security is now an integral part of the roadmap of industrial companies and operators of critical infrastructures. Now is the time to set the right course and invest the increased budget in effective OT security solutions.
More at Sophos.com
About OTORIO OTORIO is an OT (Operational Technology) security company providing end-to-end solutions for proactive digital risk management. These help industrial companies around the world to maintain business continuity and protect ongoing operations. OTORIO provides comprehensive security risk assessment, monitoring and management solutions and services for critical infrastructure, intelligent transportation and logistics systems and industrial manufacturing companies.
