A new report reveals that enterprise security operation centers (SOCs) are looking to extend detection and response into the OT space. However, a lack of employee visibility and knowledge poses significant barriers, according to a study by Trend Micro.
According to the study by the Japanese cybersecurity provider, half of the companies now have an SOC that shows a certain degree of ICS/OT (Industrial Control Systems / Operational Technology) transparency. However, even among surveyed organizations that have a broader SOC, only about half (53 percent) of their OT environment feeds data for detection purposes.
OT environment not visible in SOC
This deficit is also reflected in another study result. Cyber incident detection (63 percent) is the top skill respondents want to integrate across IT and OT silos. This is followed by inventory of existing assets (57 percent) and identity and access management (57 percent). Detecting events in IT and OT environments comprehensively and at an early stage is crucial for root cause identification and threat prevention.
The report emphasizes the importance of endpoint detection and response (EDR) and internal network security monitoring (NSM) in providing data on the root causes of cyberattacks. However, less than a third (30 percent) of the companies surveyed use EDR on both engineering systems and production systems. NSM is used even less frequently (<10 percent) at the physical process and fundamental control level in OT environments.
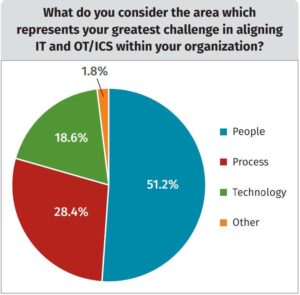
Difficult extension of SecOps to IT and ICS/OT environments
Aside from the gaps in visibility, the study also reveals that extending Security Operations (SecOps) to IT and ICS/OT environments comes with major human and procedural challenges. Four of the top five barriers identified by respondents address the issue of human resources:
- Training IT staff in OT security (54 percent)
- Communication silos between relevant departments (39 percent)
- Hiring and retention of cybersecurity professionals (38 percent)
- Train OT staff on IT (38 percent)
- Insufficient risk transparency between IT and OT areas (38 percent)
Outdated technology also creates visibility difficulties: The technical limitations of legacy devices and networks (45 percent) and IT technologies that are not designed for OT environments (37 percent) crystallize alongside the lack of OT knowledge of IT employees (40 percent) as the biggest problems.
Poll clear: OT needs to be more visible
Going forward, respondents want to redouble their efforts for better security convergence across IT and OT, thereby gaining better visibility into OT threats. Two-thirds (67 percent) plan to expand their SOC, and those already using EDR (76 percent) plan to do so in the next 24 months to ICS/OT as well. In addition, 70 percent of companies that have already introduced NSM capabilities plan to expand this technology in the same timeframe.
“IT-OT convergence is already driving digital transformation in many industrial companies. However, to effectively manage risk in these environments, the IT and OT SecOps must also converge,” explains Udo Schneider, IoT Security Evangelist at Trend Micro. "OT security programs may still be lagging behind, but present an opportunity to close the visibility and capability gap by consolidating on a single SecOps platform like Trend Vision One."
More at TrendMicro.com
About Trend Micro As one of the world's leading providers of IT security, Trend Micro helps create a secure world for digital data exchange. With over 30 years of security expertise, global threat research, and constant innovation, Trend Micro offers protection for businesses, government agencies, and consumers. Thanks to our XGen™ security strategy, our solutions benefit from a cross-generational combination of defense techniques optimized for leading-edge environments. Networked threat information enables better and faster protection. Optimized for cloud workloads, endpoints, email, the IIoT and networks, our connected solutions provide centralized visibility across the entire enterprise for faster threat detection and response.