Armis identifies and publishes a study on the most risky OT and ICS devices in critical infrastructure. It shows the threats to critical infrastructure in manufacturing, utilities and transportation.
The one from the Armis Asset Intelligence and Security Platform Analyzed data monitoring more than three billion assets found that the operational technology (OT) and industrial control systems (ICS) devices that pose the greatest risk to these industries are engineering workstations, SCADA servers, automation servers, data historians, and programmable logic controllers (PLC).
Prioritization and vulnerability management remain an issue
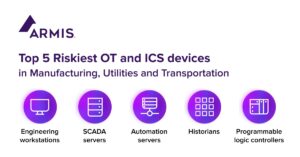
🔎 The report identifies the top 5 most vulnerable OT and ICS devices in the enterprise (Image: Armis).
Research found that technical workstations saw the most attack attempts in the industry over the past two months, followed by SCADA servers. 56 percent of technical workstations have at least one unpatched critical vulnerability (Common Vulnerabilities and Exposures (CVEs)) and 16 percent are vulnerable to at least one dangerous CVE that was published more than 18 months ago.
Uninterruptible power supplies (UPS) are the third type of device that has been attacked the most in the past two months. Although critical for continuity in the event of a power outage, the data showed that 60 percent of UPS devices have at least one unpatched CVE vulnerability with critical severity, which, like TL Storm has shown could trick cybercriminals into damaging the device itself or other assets connected to it.
SPS: 40 percent of the controllers are unpatched
Another example is programmable logic controllers (PLCs), of which 41 percent have at least one unpatched CVE with critical severity. These legacy devices are critical because an attack could disrupt core operations. However, research has shown that they may be susceptible to high risk factors. An example of this is hardware or firmware that is no longer supported.
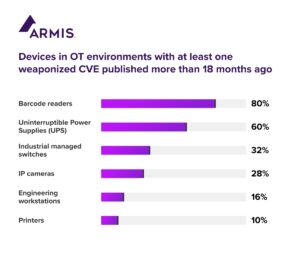
A number of other devices pose a risk to manufacturing, transportation, and utility environments because they had at least one malicious CVE released prior to January 2022: 85 percent of barcode readers, 32 percent of industrial managed switches, 28 percent of IP cameras and 10 percent of printers.
IP cameras and printers are also at risk
Across industries, OT companies are characterized by having multiple sites, multiple production lines, and complex distribution lines with large numbers of managed and unmanaged devices on their networks. In this context, understanding where the risk comes from and what remedial actions are required is a major challenge. This can be an obstacle to vulnerability management and provides an entry point for threat actors.
"Vulnerable devices are common in an ICS environment, so professionals need to see what assets are on their network and additional information about what those devices are actually doing," said Nadir Izrael, CTO and co-founder of Armis. “With contextual data, teams can define what risk each device poses to the OT environment, allowing them to prioritize remediation of critical and/or exploitable vulnerabilities to rapidly reduce the attack surface.”
There is a need for collaboration between OT and IT teams
Industries with OT have changed significantly in recent years due to the convergence of OT and IT. This convergence ushers in a new phase of the industrial age and enables cross-discipline collaboration, but in practice unified management of both environments has yet to happen. As OT teams focus on maintaining industrial control systems, mitigating risks to OT, and ensuring overall integrity within operational environments, the more IT-related tasks have been neglected.
Four of the top five risky devices run Windows operating systems, showing that a basic understanding of asset risk and securing vulnerable assets is still a challenge for IT and OT teams.
SMBv.1 protocol vulnerability further found
Armis studied device types and found that many of them are more vulnerable to malicious activity because they use the SMBv.1 protocol, outdated operating systems, and many open ports. SMBv.1 is an outdated, unencrypted and complicated protocol with vulnerabilities targeted in the notorious Wannacry and NotPetya attacks. Security experts previously advised companies to stop using this protocol, but data shows it is still being used in this space.
“From an organizational perspective, a risk-based approach to vulnerability management must go hand-in-hand with OT and IT departments working together to coordinate mitigation efforts,” says Izrael. “Cross-departmental projects help streamline processes and resource management, and improve compliance and data security. To meet the challenges of the new industrial age, security professionals need an IT/OT convergence security solution that protects all assets connected to the network.”
A platform that searches all compromised devices
The Armis Unified Asset Intelligence platform discovers all connected assets, maps out the communications and relationships between them, and adds contextual information to understand their context and the risk they may pose to the organization. It is purpose-built to protect OT and IT environments and can capture meaningful signals from hundreds of IT and OT platforms. The cloud-based threat detection engine uses machine learning and artificial intelligence to detect when a device is operating outside of its normal, known-good state and triggers an automated response to help manage the entire attack surface.
methodology
Armis calculated device risk by looking at all devices on the Armis Asset Intelligence and Security platform and determining which types had the highest risk factor and/or the most common vulnerabilities and exposures (CVEs). In addition, the level of business impact and endpoint protection had a weighted impact on the results.
More at Armis.com
About Armis
Armis, the leader in asset visibility and security, offers the industry's first unified asset intelligence platform that addresses the new, expanded attack surface created by connected assets. Fortune 100 companies trust our real-time and continuous protection to protect all managed and unmanaged assets across IT, cloud, IoT devices, medical devices (IoMT), operational technology (OT), industrial control systems (ICS) and 5G seen in full context. Armis provides passive cyber asset management, risk management, and automated enforcement. Armis is a private company headquartered in California.