Industrial cybersecurity - ICS: New report shows significant increase in reported vulnerabilities in IoT, IT and medical devices. A third of the vulnerabilities increasingly affect the extended Internet of Things (XIoT). ICS security needs to be extended to these systems as well.
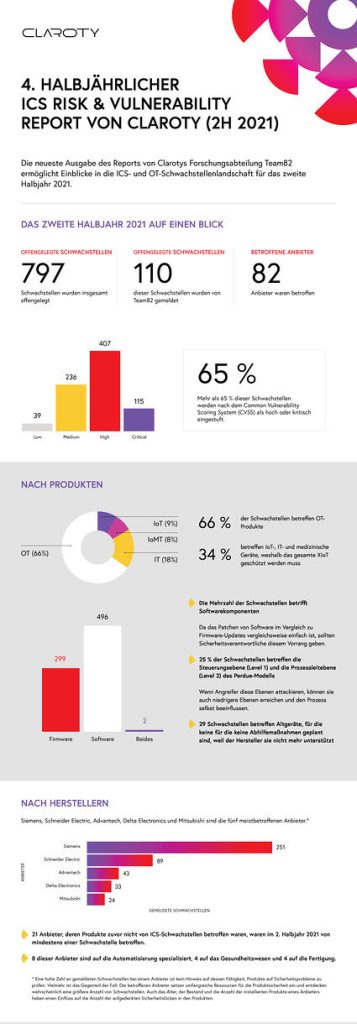
The disclosure of vulnerabilities in industrial control systems (ICS) has more than doubled (up 110%) in the last four years, with the number increasing by 2021 percent in the second half of 25 alone compared to the previous six months. This comes from the fourth biannual ICS Risk & Vulnerability Report released today by Claroty, specialist in cyber-physical systems (CPS) security in industrial, healthcare and enterprise environments. The study also shows that ICS vulnerabilities extend beyond operational technology (OT) to the extended Internet of Things (XIoT): 34 percent of the discovered vulnerabilities were related to IoT, medicine (Internet of Medical Things/IoMT) and IT -Systems.
ICS: Vulnerabilities in OT, XIoT and IT systems
The report provides a comprehensive analysis of ICS vulnerabilities released in H2021 82, including those uncovered by Claroty's award-winning research team TeamXNUMX, as well as those sourced from trusted open sources. These include the National Vulnerability Database (NVD), the Industrial Control Systems Cyber Emergency Response Team (ICS-CERT), CERT@VDE, MITER and the industrial automation providers Schneider Electric and Siemens.
"As more and more cyber-physical systems become interconnected and access to these networks takes place over the internet and the cloud, security leaders need timely, useful vulnerability intelligence to adjust their risk management accordingly," said Amir Preminger, Vice President of Research at Claroty. “The increasing digital transformation coupled with the convergence of ICS and IT infrastructure enables researchers to extend their work beyond OT to the XIoT. High-profile cyber incidents in the second half of 2021, such as the Tardigrade malware, the Log4j vulnerability or the ransomware attack on petrol station supplier Oiltanking, show the vulnerability of these networks and underscore the need for security researchers to work together to discover and disclose new vulnerabilities.”
Main findings of the report
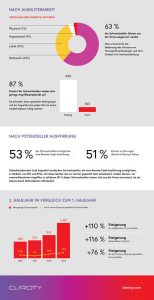
- The number of disclosed ICS vulnerabilities has increased by 110 percent in the last four years. This shows that awareness of this topic has increased significantly and security researchers are increasingly including OT environments as well. 797 vulnerabilities were reported in the second half of 2021, a 25 percent increase from 637 in the first half of 2021.
- 34 percent of the discovered vulnerabilities concern IoT, IoMT and IT components. That's why companies need to bring OT, IT and IoT together under convergent security management. Operators of these systems need an accurate view of their environments to manage vulnerabilities and mitigate their exposure.
- Half of the vulnerabilities (50%) were discovered by external specialists, most of them by researchers from cybersecurity companies shifting their focus to ICS alongside IT and IoT security research. In addition, 55 new researchers reported security vulnerabilities.
The number of vulnerabilities reported by internal experts has increased by 76 percent over the past four years. This underlines the growing importance of the discipline and a higher degree of maturity in vulnerability research and shows that manufacturers are dedicating ever greater resources to the security of their products. - 87 percent of vulnerabilities have low attack complexity, meaning they don't require special conditions and attackers can count on repeatable success every time. 70 percent do not require special permissions to successfully exploit a vulnerability, and 64 percent of vulnerabilities do not require user interaction.
- 63 percent are remotely exploitable. This shows that securing remote connections and devices is of the utmost importance as the need for secure remote access solutions, accelerated by the pandemic, continues.
Claroty's research department, Team82, remains at the forefront of ICS vulnerability research, uncovering 2021 vulnerabilities in the second half of 110 and over 260 vulnerabilities in total. - The most common potential impact is remote code execution (accounting for 53% of vulnerabilities), followed by disruption (denial of service) (42%), protection evasion (37%), and opportunities for attackers to read application data (33%).
- Top mitigations include network segmentation (recommended for 21% of vulnerabilities), protection against ransomware, phishing and spam (15%) and traffic throttling (13%).
The full findings, in-depth analysis and additional measures to protect against unauthorized access and risk can be found in Claroty's semi-annual ICS Risk & Vulnerability Report. This can be downloaded online for free.
More at Claroty.com
About Claroty Claroty, the Industrial Cybersecurity Company, helps its global customers discover, protect and manage their OT, IoT and IIoT assets. The company's comprehensive platform can be seamlessly integrated into customers' existing infrastructure and processes and offers a wide range of industrial cybersecurity controls for transparency, threat detection, risk and vulnerability management and secure remote access - with significantly reduced total cost of ownership.