Trend Micro's Pwn2Own brings well-known technology manufacturers together and promotes vulnerability research. The hacking competition thus increases security for around 1 billion end users. Participating as partners: Microsoft, Tesla, Zoom and VMware. There was also 1 million in prize money.
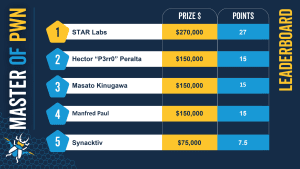
Trend Micro, one of the world's leading providers of cyber security solutions, is once again positioning itself as a technology innovator with the hacking event Pwn2Own. On the occasion of the 15th anniversary of the event, 25 zero-day vulnerabilities were uncovered at software providers. These include the partners Microsoft, Tesla, Zoom and VMware. The participants were rewarded for their efforts with prize money of more than one million euros.
25 zero-day vulnerabilities discovered
The annual hacking competition brings together security researchers from around the world to target enterprise software and uncover vulnerabilities in commonly used applications. Even before cybercriminals can abuse them, providers get the chance to close the security gaps. The target software is selected from the areas that are particularly critical for companies and private individuals worldwide.
"The researchers who participate in Pwn2Own influence our security strategy," said Aanchal Gupta, CVP, Azure and M365 Security at Microsoft. “Our team always learns from the attendees who find bugs and demonstrate exploits during the event. Pwn2Own is raising the bar for the entire industry and we are very excited to be a part of this event.
Zero Day Initiative (ZDI)
Trend Micro's Zero Day Initiative (ZDI) organizes the event and works with the world's leading technology manufacturers to make the IT landscape more secure overall. Identifying new attack vectors, such as how critical applications can be abused by cybercriminals, forms the basis of Trend Micro's security portfolio. This includes safety solutions for the automotive industry.
“Home office and electric cars will continue to accompany us in the future. That's why we want to ensure that the software, as the driver of the future technology landscape, is also secure - regardless of the type and location of the end device," says Kevin Simzer, COO of Trend Micro. The insights gained at Pwn2Own are not only valuable for us and our customers. They serve the entire IT community and all users.”
More at TrendMicro.com
About Trend Micro As one of the world's leading providers of IT security, Trend Micro helps create a secure world for digital data exchange. With over 30 years of security expertise, global threat research, and constant innovation, Trend Micro offers protection for businesses, government agencies, and consumers. Thanks to our XGen™ security strategy, our solutions benefit from a cross-generational combination of defense techniques optimized for leading-edge environments. Networked threat information enables better and faster protection. Optimized for cloud workloads, endpoints, email, the IIoT and networks, our connected solutions provide centralized visibility across the entire enterprise for faster threat detection and response.