
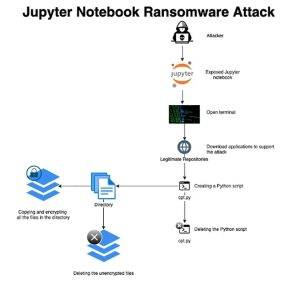
Team Nautilus, Aqua Security's research unit specializing in the cloud-native technology stack, has discovered a new attack vector that cybercriminals can use to target companies running ransomware. For the first time, the team uncovered a Python-based ransomware attack targeting the open source software Jupyter Notebook, popular with data professionals.
Attackers first gain access through misconfigured environments and then run a ransomware script that encrypts every file in a specified path on the server and then deletes itself after execution to obfuscate the attack. Because Jupyter Notebook is used to analyze data and create data models, this attack can cause significant damage to organizations if these environments are not properly secured.
Businesses and researchers are at risk
Researchers set up a honeypot using an internet-connected Jupyter application designed to simulate a real-world corporate environment. It thus included access to real instances of Jupyter Notebooks and raw data that the attacker could encrypt. Tracee of Aqua Security, an open source runtime security and forensics tool for Linux, was used to detect the attack.
Cyber criminals use the popular Jupyter software to attack notebooks with ransomware (Image: Aqua Security).
There are some recommendations for Jupyter Notebook users to protect against this method
- Use tokens or another authentication method to control access to your data development application.
- Make sure you use SSL to protect data in transit.
- Limit inbound traffic to the application either by completely blocking internet access or, if the environment requires internet access, use network rules or VPN to control inbound traffic. It is also recommended to restrict outbound access.
- Run your applications with an unprivileged user or a user with limited rights.
- Be sure you know all the Jupyter notebook users. You can query the users in a Sqlite3 database which you should find in the following path: './root/.local/share/jupyter/nbsignatures.db'. If SSH access to the server is enabled, you can also check the authorized SSH key files to make sure you know all the keys and that there are no unknown users or keys.
Aqua Security has published a detailed blog detailing Team Nautilus' honeypot and the kill chain of observed attacks: Threat Alert: First Python Ransomware Attack Targeting Jupyter Notebooks.
More at Aquasec.com
About Aqua Security
Aqua Security is the largest pure cloud native security provider. Aqua gives its customers the freedom to innovate and accelerate their digital transformation. The Aqua platform provides prevention, detection, and response automation across the application lifecycle to secure the supply chain, cloud infrastructure, and ongoing workloads—regardless of where they are deployed.
