In its investigation, Sophos explains how liquidity mining – the latest cryptocurrency investment craze – is being used as a platform by cybercriminals. "The mechanics of liquidity mining, in its legitimate form, provide the perfect camouflage for what are essentially old-fashioned scams, reimagined for the cryptocurrency age." Sean Gallagher, Senior Threat Researcher, Sophos.
With the article Liquidity Mining Scams Add Another Layer to Cryptocurrency Crime, Sophos kicks off a series of how scammers are exploiting the hype around cryptocurrency trading to lure and scam potential investors.
In the article, Sophos explains how the complexities of cryptocurrencies and decentralized finance (DeFi) - the fundamentals of liquidity mining - create the ideal environment for criminals to disguise and carry out their nefarious intentions. Potential victims are cleverly targeted. Recipients proactively receive direct message spam messages on Twitter, What's App, Telegram and other social networking platforms, initially chatting harmlessly about liquidity mining. Step by step, the criminals then escalate their perfidious swindle.
Direct message led to multiple scammer groups
By investigating interactions within a single direct message on Twitter, Sophos uncovered several liquid mining scammer groups. "Liquidity mining is a form of cryptocurrency investment in DeFi that, even when 'legitimate', is both dubious and complicated," said Sean Gallagher, senior threat researcher at Sophos. “The strategies behind the investments themselves are complex and there is no regulation beyond the 'smart contract' code embedded in the DeFi network's blockchain - code that many people cannot easily interpret, even if it is made public .
Also, new investors lack reliable information on how these networks work. Despite these risks, liquidity mining is the latest cryptocurrency investment craze, but these factors also make it the perfect platform for scammers. Unfortunately, we expect that Liquidity Mining CryptoCrime will continue; it has not yet reached its peak. Hundreds of millions of dollars are at stake."
How Liquidity Mining works
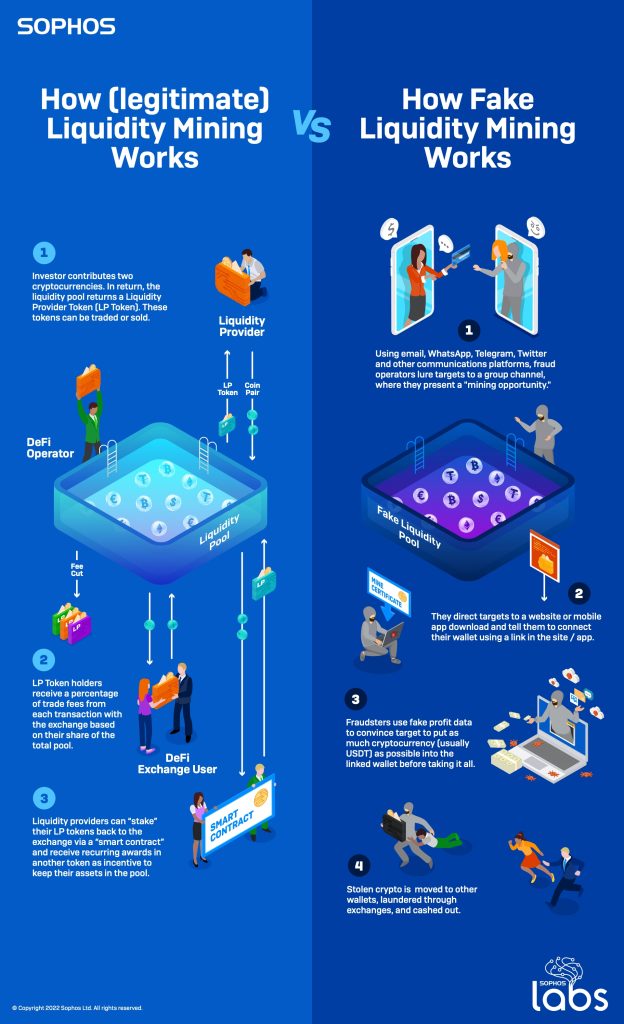
Legitimate liquidity mining allows DeFi networks to automatically settle trades in digital currencies like Ethereum, the cryptocurrency of choice for liquidity mining. Smart contracts integrated into the DeFi network need to quickly determine the relative value of the exchanged currencies and execute the trade. Since there is no central pool of cryptocurrencies for these decentralized exchanges (DEX) to draw from to close deals, they rely on crowdsourcing to provide the pool of cryptocurrency capital needed to close a deal - one liquidity pool.
To create the liquidity pool that handles transactions between cryptocurrencies, such as Ethereum and Tether, investors put the equal value of both cryptocurrencies into the pool. In exchange for committing this cryptocurrency to the pool, investors receive compensation based on a percentage of the trading fees associated with the DeFi protocol.
Investors will also receive liquidity pool tokens (LP tokens) representing their share of the pool. These tokens can be “hedged” or linked to the exchange, further tying up the original contribution and giving the investor dividends in the form of another cryptocurrency associated with the DeFi project. The value of these reward tokens can vary widely.
The scam is old
“The mechanics of liquidity mining, in its legitimate form, provide the perfect camouflage for what are essentially old-fashioned scams reimagined for the cryptocurrency age,” says Sean Gallagher. “Like traditional Ponzi schemes, criminal liquidity mining schemes give targets the illusion that they can withdraw their funds at any time and even allow them to make early withdrawals. However, the scam gangs constantly push the targets to keep investing and 'invest big' by disguising the real operations with fake applications, fake earnings reports and promises of lucrative payouts.
In reality, the scammers have taken control of their targets' cryptocurrency wallets and withdraw the currency whenever they want. Little by little, scammers empty wallets while continuing to reassure targets that everything is fine before eventually cutting off communication.”
Fraudsters empty their wallets
Sophos does not anticipate that despite the recent cryptocurrency crash and current volatility, overall liquidity mining will be hampered as Tether returns to near par and other cryptocurrencies recover. "The criminal economy is still powered by cryptocurrency, and there is enough interest in cryptocurrency to keep liquidity mining and similar scams afloat," said Sean Gallagher.
More at Sophos.com
About Sophos More than 100 million users in 150 countries trust Sophos. We offer the best protection against complex IT threats and data loss. Our comprehensive security solutions are easy to deploy, use and manage. They offer the lowest total cost of ownership in the industry. Sophos offers award-winning encryption solutions, security solutions for endpoints, networks, mobile devices, email and the web. In addition, there is support from SophosLabs, our worldwide network of our own analysis centers. The Sophos headquarters are in Boston, USA and Oxford, UK.