Europol has investigated many areas of cybercrime and produced an interesting report, which, however, only highlights individual areas. The so-called Spotlight report will be presented as part of IOCTA 2023 – Internet Organized Crime Threat Assessmen.
The Spotlight report, “Cyberattacks: the pinnacle of crime-as-a-service,” examines developments in cyberattacks and discusses new methods and threats observed by Europol’s operational analysts. It also explains the types of criminal structures behind cyberattacks and how these increasingly professionalized groups are exploiting changes in geopolitics as part of their methods.
This report is the first in a series of spotlight reports published by Europol Published as part of IOCTA 2023 (Internet Organized Crime Threat Assessmen). has. Each takes a closer look at emerging trends in a specific area of cybercrime. Other IOCTA 2023 modules address online fraud and child sexual exploitation.
Key findings from the Spotlight report
- Malware-based cyberattacks, particularly ransomware, remain the largest threat with wide reach and significant financial impact on the industry.
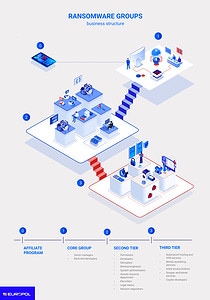
- Ransomware affiliate programs have emerged as the primary form of business organization for ransomware groups that continue to use multi-pronged extortion methods, and there are signs that the theft of sensitive information may become the primary threat.
- Phishing emails containing malware, brute-forcing via Remote Desktop Protocol (RDP), and exploiting Virtual Private Network (VPN) vulnerabilities are the most common attack tactics used by cybercriminals. It then abuses legitimate software and tools built into operating systems to build persistence and penetrate their victims' networks.
- Russia's war of aggression against Ukraine led to a significant increase in DDoS (Distributed Denial of Service) attacks against EU targets. The most prominent DDoS attacks were politically motivated and coordinated by pro-Russian hacker groups.
- Initial Access Brokers (IABs), Dropper-as-a-Service and Crypter developers are key enablers for executing a variety of cyberattacks. High-level cybercriminals are benefiting greatly from increasing activity on criminal marketplaces and IABs selling stolen data.
- The war of aggression against Ukraine and Russia's domestic politics have uprooted cybercriminals and pushed them to move to other jurisdictions.