The MustachedBouncer hacker group from Belarus is spying on various foreign embassies in Belarus. The attacks target the data of diplomats and embassy employees. ESET specialists discovered the attacks.
MoustachedBouncer, a previously unknown cyberespionage group recently discovered by ESET Research, has been spying on foreign embassies in Belarus since at least 2014. She operates in tandem with another group called the Winter Vivern. The attacks are based on the Adversary-in-the-Middle (AitM) method. ESET experts suspect that the hackers are conducting their attacks at the Internet Service Provider (ISP) level. The masterminds behind MoustachedBouncer aim to compromise embassy employees' computers and siphon off data. The focus is on stealing files and monitoring internal and external drives. Since the group is acting in the interests of Belarus, Belarusian authorities are believed to have gained access to the hijacked data.
What is an Adversary-in-the-Middle Attack?
An Adversary-in-the-Middle (AitM) attack is a type of cyberattack in which an attacker positions themselves in the communication between two parties. This can be two users, two devices, or one user and one application or one server. Up to this stage, the attack resembles the man-in-the-middle (MitM) technique. In addition, the hacker takes control of the underlying network infrastructure and is thus able to actively manipulate the network. This gives him access to all sent and received information. Just last year, a large-scale AitM campaign made headlines when hackers obtained login data and thus access to numerous Microsoft Office accounts - despite security measures such as multi-factor authentication.
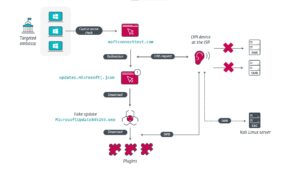
“In order to compromise their targets, MoustachedBouncer actors manipulate their victims' Internet access. They then trick the operating system into believing that it is behind a company-owned portal. For the IP ranges that MoustachedBouncer targets, network traffic is redirected to a seemingly legitimate but fake Windows update page,” explains ESET researcher Matthieu Faou, who discovered the new cyberespionage group. “This 'adversary-in-the-middle' variety only occurs in a select few organizations, perhaps only in embassies and not nationally. The AitM scenario is reminiscent of the hacker groups Turla and StrongPity, who infected software installers with trojans at the ISP level,” adds Faou.
These spy tools are used
MoustachedBouncer uses two separate toolsets in parallel, which ESET researchers have dubbed NightClub and Disco. NightClub uses free email service Seznam.cz from Czech Republic and webmail provider Mail.ru from Russia to exfiltrate data. Other features include creating audio recordings and screenshots, and submitting keystrokes. Only one of the two toolsets is used on a single computer:
- Disco is used in conjunction with AitM attacks.
- NightClub is used for victims where traffic interception at the ISP level is not possible because a protective measure is in place – for example, an end-to-end encrypted VPN that manages internet traffic outside of Belarus.
The majority of private users rely on a modern operating system (47 million). Nevertheless, around six percent of users are on the Internet with an outdated system (2,95 million).
Cooperation with another hacker group
ESET believes that MustachedBouncer is working with another hacking group called Winter Vivern. The group had previously targeted government officials from several European countries, including Poland and Ukraine, earlier this year.
“Diplomats are a highly vulnerable group of people and an attractive target for politically motivated hackers. If embassy employees work in politically unstable countries such as Belarus, they must therefore use an encrypted VPN tunnel to a trustworthy location for all their Internet traffic. Also, they should use quality and up-to-date computer security software. This is the only way they can escape surveillance,” advises Faou.
More at ESET.com
About ESET ESET is a European company with headquarters in Bratislava (Slovakia). ESET has been developing award-winning security software since 1987 that has already helped over 100 million users enjoy secure technology. The broad portfolio of security products covers all common platforms and offers companies and consumers worldwide the perfect balance between performance and proactive protection. The company has a global sales network in over 180 countries and branches in Jena, San Diego, Singapore and Buenos Aires. For more information, visit www.eset.de or follow us on LinkedIn, Facebook and Twitter.