
Trend Micro introduces new endpoint security solution for industrial control systems (ICS). The solution was specially developed to embed ICS environments without interruption in a comprehensive cybersecurity concept.
Trend Micro, one of the world's leading providers of cybersecurity, introduces the first OT-native endpoint security solution of its kind, which is offered as part of a comprehensive security solution for smart factories. TXOne StellarProtectTM was developed by TXOne Networks to protect all OT endpoints, regardless of the respective environmental conditions, in business-critical Industrial Control System (ICS) environments.
Smart factory environments offer attack surfaces
The large number of ICS endpoints in smart factory environments offers numerous attack surfaces, as they often also include unpatched or otherwise vulnerable devices. A disruption of these endpoints causes considerable impairment in production and can endanger the entire operation. According to the Trend Micro 2020 Annual Cybersecurity Report, the manufacturing industry is a prime target for highly infectious ransomware attacks. It is therefore more important than ever to protect the systems with technologies that are specially designed for this area of application.
"The unpleasant reality of ICS endpoint security is that there has not yet been a security solution that was specially developed for the requirements of modern systems in the OT environment in terms of high availability," says Udo Schneider, IoT Security Evangelist Europe at Trend Micro. "Cybersecurity solutions for ICS endpoints must consider three factors to meet industry requirements: they must have little impact on performance, must run non-disruptively, and provide comprehensive protection in any environment."
Machine learning instead of updates
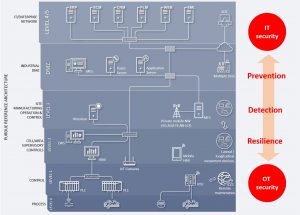
The cybersecurity solution for the Smart Factory TXOne StellarProtectTM uses IT and OT security to protect industrial endpoints (Image: Trend Micro).
The special requirements of the shop floor environment for solutions that protect operations without affecting performance at the same time represent a challenge. Conventional solutions such as signature-based antivirus programs can identify known threats, but require a constant Internet connection and frequent updates - which is the case critical systems cannot be implemented. Advanced machine learning (ML) -based solutions are able to quickly detect anomalies and unknown threats, but bring with them a large number of false positives that can affect ongoing operations. While application control or lockdown-based solutions are leaner and their safelist simplifies provision, they also limit a machine to a special purpose and are therefore only suitable for systems with a very specific use. Although these individual product solutions provide many helpful services, they are not able to offer the flexibility required to both ensure the operational reliability of production plants and to guarantee it in the long term.
TXOne StellarProtectTM for ICS endpoint security
TXOne StellarProtectTM uses machine learning and ICS Root of Trust to offer a unique ICS-native endpoint security against known and still unknown malware. To avoid redundant security scans and poor performance, ICS Root of Trust collects over 1.000 ICS software certificates and licenses and verifies them in advance. Due to the Least Privilege Policies applied, StellarProtect does not depend on an Internet connection to fend off malware-free attacks. Production interruptions due to malicious attacks or operating errors by employees are prevented by the integrated behavior learning engine of ICS applications.
"ICS endpoint security solutions have to adapt to the requirements of OT environments and not the other way around," explains Udo Schneider. “TXOne StellarProtect sets a new standard for endpoint security in industrial control systems. We look forward to helping our customers minimize cyber risks in their OT environments without disruption or need for adjustment. "
More at TrendMicro.com
About Trend Micro As one of the world's leading providers of IT security, Trend Micro helps create a secure world for digital data exchange. With over 30 years of security expertise, global threat research, and constant innovation, Trend Micro offers protection for businesses, government agencies, and consumers. Thanks to our XGen™ security strategy, our solutions benefit from a cross-generational combination of defense techniques optimized for leading-edge environments. Networked threat information enables better and faster protection. Optimized for cloud workloads, endpoints, email, the IIoT and networks, our connected solutions provide centralized visibility across the entire enterprise for faster threat detection and response.
Matching articles on the topic
