Identity-based attacks that abuse compromised credentials to access resources are a blind spot in enterprise security defenses. For example, while there are real-time protection solutions against various types of attacks such as malware, malicious data access and its exfiltration, there is no protection against a scenario in which attackers authenticate themselves with valid but compromised credentials.
A paradigm shift is therefore required to counter these attacks effectively. User identities must be treated as distinct attack vectors with specific characteristics and properties. This article examines why existing security portfolios fail against identity-based attacks and what measures companies can take to protect themselves against these threats.
Overview of common identity-based attacks
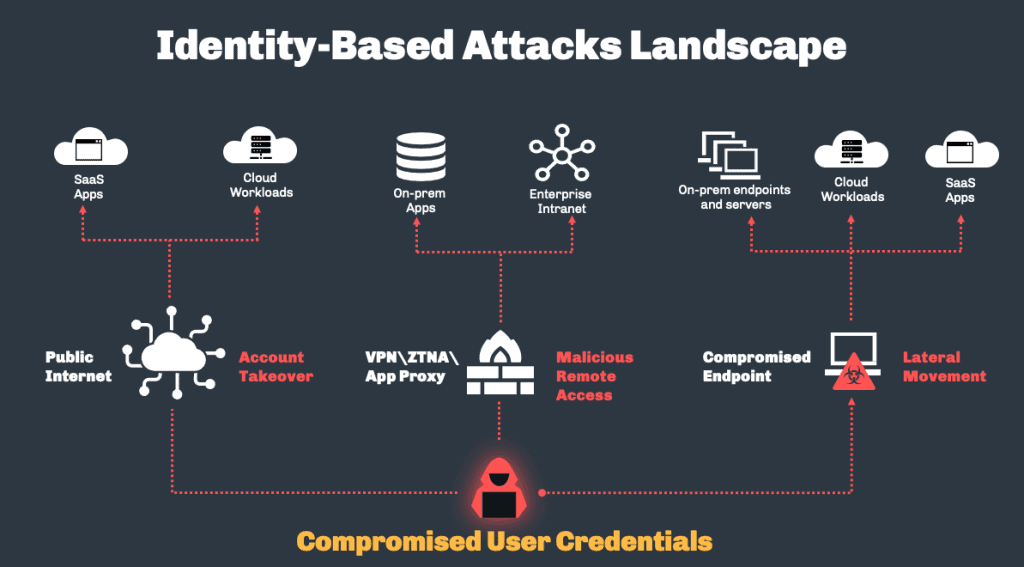
Identity-based attacks using compromised credentials to access target resources can be a standalone act, such as brute-forcing a SaaS application, or they can be part of a broader attack, such as a hacker's lateral movement in the on-premises network. The following diagram summarizes the common identity-based attacks that organizations typically encounter.
Fast growing attack vector
According to security firm Digital Shadows' 2020 report From Exposure to Takeover, there are over 15 billion credentials floating around on the dark web for sale. This number gives some indication of the magnitude of the problem facing companies around the world.
The IBM Cost of a Data Breach Report 2021 also finds that the most common initial attack vector in 2021 was compromised credentials. These were responsible for 20 percent of security breaches, maintaining their lead from the previous year. In addition, the report states that security breaches caused by stolen/compromised credentials took the longest time to identify (at 250 days) and containment (91 days) on average, for a total average duration of 341 days . It should also be noted that business email compromise, which the report found to be the most costly attack vector, is essentially a special case of compromised credentials.
Inconsistent protections and blind spots
Identity-based attacks encounter weaknesses in today's security system. First, protection is distributed across different products and teams – CASB to protect against first-time access to SaaS applications, Endpoint Protection Platform (EPP) against local lateral movement, Next Generation Firewalls against malicious remote connections, and so on. Second, all of these security measures are inherently incapable of providing real-time protection against malicious authentication with compromised credentials. The reason for this is simple: This is not what these products were designed for.
Real-time protection is key
The core of any cyber protection is based on the following capabilities:
- Monitoring of a specific activity within the IT environment.
- Detection of malicious behavior in this activity.
- Termination of activity if detected as malicious.
The key security requirement is therefore the ability to protect in real-time, blocking malicious activity as soon as it is detected.
An example of how this concept can be illustrated is with an Endpoint Protection Platform (EPP) solution: An EPP agent is installed on a workstation or server and can monitor all running processes, detect that a specific process is exhibiting malicious behavior, and terminate the process entirely if necessary. The solution was developed for this. And indeed, EPP does a great job of stopping exploits, malware, scripts, malicious macros, and any threat that manifests itself as anomalous process behavior.
The essential value of EPP is that it is placed where it can stop malicious activity in real-time. This also applies to other security products, each in their own area - firewalls for network traffic, DLP for file access, and more.
Real-time protection against identity-based attacks
Identity-based attacks use compromised credentials to perform what appears to be legitimate authentication. Therefore, to provide real-time protection against this type of threat, one must be able to not only reliably flag an authentication attempt as malicious, but also proactively prevent it. This task is beyond the scope of any classic security product, as none of them are designed to participate in the authentication process.
For example, if a hacker carries out a lateral movement attack using PsExec to spread from the patient zero computer to additional computers, the agent of an endpoint protection platform can detect that a PsExec process is running. However, the agent plays no part in the full authentication cycle, in which the attacker on the Patient Zero machine submits compromised credentials to Active Directory in order to log on to another machine. Even if the agent could detect that a particular authentication is indeed malicious, it could do nothing about it.
Real-time identity protection starts with the identity provider
In fact, the only components in today's environment that can enforce this type of protection are the identity providers themselves, as they are at the core of all authentication activities. And this applies to any type of resource: to prevent account takeover on SaaS applications, the existing cloud identity provider should be used. To prevent the automatic spread of ransomware, the on-premises directory (in most cases Active Directory) should be used.
The problem is that in most cases, identity providers do not go beyond validating the password they receive. If the attacker on the Patient Zero machine tries to access another computer with compromised credentials, Active Directory will not be able to detect that the valid credentials provided are being misused.
For example, while identity providers are a key component in providing real-time protection against identity-based attacks, they cannot fully provide that protection in their current form.
New technology closes the security gap
Unified Identity Protection is a novel technology that natively integrates with all existing identity providers to add both risk analysis and proactive prevention capabilities in addition to initial login verification by the identity provider. Whenever an identity provider receives an access request, it is forwarded to the Unified Identity Protection solution for verification.
By retrieving this data from all of the enterprise's identity providers, the solution obtains each user's full authentication activity across all resources. With this complete data, the technology can then analyze the risk of each authentication attempt. Based on the analysis results, a risk engine decides whether or not the user is allowed to access the requested resource and whether they should go through multi-factor authentication. Based on this, the responsible identity provider then grants or denies the user access. This unified approach enables protection against any type of identity-based attack to be centralized.
The blind spot in today's defense stems from the mindset of viewing attacker lateral movement as an endpoint issue, SaaS account takeover as a SaaS access issue, and malicious remote access to a network as a network issue. In essence, however, all of these examples are different manifestations of a compromised credentials threat. A problem that can only be solved by placing security controls where authentication and access attempts actually take place.
More at Silverfort.com
About Silverfort Silverfort is the provider of the first Unified Identity Protection Platform that consolidates IAM security controls in corporate networks and cloud environments in order to ward off identity-based attacks. Through the use of innovative agent-free and proxy-free technology, Silverfort integrates seamlessly into all IAM solutions, standardizes their risk analysis and security controls and extends their coverage to assets that previously could not be protected, such as self-developed and legacy applications, IT infrastructure , File systems, command-line tools, machine-to-machine access and more.