The volume of DDoS attacks (Distributed Denial of Service) increased by 40 percent worldwide in the second quarter compared to the same period last year. This is one of the key findings of Radware's quarterly DDoS Attack Report. The report provides an overview of DDoS attack trends by industry as well as by application and attack type.
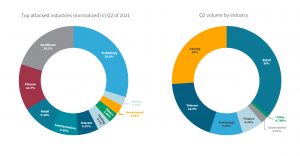
Geographically, the attacks were mainly spread across America and the EMEA region, which accounted for 80 percent of the volume. In terms of industries, the focus was primarily on technology companies with an average of almost 3.000 attacks, followed by healthcare with around 2.000 attacks per company. However, the attack volumes in these two industries were relatively small, while retail and telecommunications had to fight off a significantly lower number of attacks, which had significantly higher volumes. Only about 6 percent of all attacks were directed against telecommunications companies, but they accounted for 18 percent of the total volume. Retail was faced with around 9 percent of the attacks, but 36 percent of the attack volume. The health sector, on the other hand, had a volume of less than one percent in over 20 percent of the attacks.
Further results of the DDoS Attack Report
- On average, each company had to detect and block almost 2021 malicious events and a volume of 5.000 TB per month in the second quarter of 2,3.
- In the second quarter of 2021, the average number of malicious events blocked per company increased by more than 30%, and the average blocked volume per company increased by more than 2020% compared to the second quarter of 40.
- In the first half of 2021, a company in North and South America or in EMEA had to hold off twice as much volume on average as a company in the Asia-Pacific region (APAC). North, Central and South America as well as EMEA accounted for around 80% of the averted attack volume in the same period.
“While large-scale ransomware attacks grab the headlines, there are other cyber threats that organizations need to watch out for,” said Pascal Geenens, director of threat intelligence at Radware. “From an increase in DDoS ransomware campaigns and DDoS hit-and-run attacks to an activist group targeting financial firms in the Middle East, there was a worrying level of cyber activity in the second quarter Compared to the same quarter last year. The findings of this report should serve as a strong reminder to companies that no company is immune from being a target.”
Attackers focus on the financial sector
After technology and healthcare, the financial sector was the sector most affected by DDoS attacks in the second quarter (1.350 attacks per company), followed by retail, communications and telecommunications (between 600 and 1.000 attacks per company). The gambling industry saw an average of more than 400 attacks, while government and utilities averaged around 280. In terms of blocked volume, retail was the hardest hit in the second quarter, followed by gaming, telecommunications and technology, which blocked the second, third and fourth highest volumes, respectively.
Aggressive burst attacks against technology and financial companies
Radware's recent study also shows that there were notable burst attacks in the second quarter of 2021. These attacks targeted financial and technology companies. These “hit-and-run” DDoS attacks use repetitive short, high-volume bursts and were particularly aggressive in their amplitude (attack size) and frequency (number of bursts per unit time). One attack performed multiple consistent 80 Gbps bursts that lasted two to three minutes and repeated every four minutes. This resulted in 12 attack bursts of 80 Gbps within a 45 minute timeframe.
Malicious scanners exploit vulnerabilities
In the second quarter of 2021, companies blocked an average of almost 2.000 scan events by vulnerability scanners that they did not control themselves. According to Radware, 40 percent of these scans were performed by potentially malicious scanners that were actively exploiting known vulnerabilities and attempting to attack a company. Vulnerability scanners are automated tools that organizations can use to determine whether their networks and applications have any security vulnerabilities that could expose them to attack.
"Organizations are challenged by well-organized threat actors," Geenens said. “The window of time between discovery and exploitation of new vulnerabilities is getting smaller and smaller. In some cases, we have observed that it takes less than 24 hours between the release of a patch by a vendor and an attempt to exploit the vulnerability."
Radware's full Q2 DDoS Attack Report can be viewed here. The data for the report is based on a sample of Radware devices deployed in Radware's cloud scrubbing centers and on-premise devices in Radware Hybrid and Peak Protection Services.
More at Radware.com
About Radware Radware (NASDAQ: RDWR) is a global leader in application delivery and cybersecurity solutions for virtual, cloud and software-defined data centers. The company's award-winning portfolio secures the company-wide IT infrastructure and critical applications and ensures their availability. More than 12.500 enterprise and carrier customers worldwide benefit from Radware solutions to quickly adapt to market developments, maintain business continuity and maximize productivity at low cost.