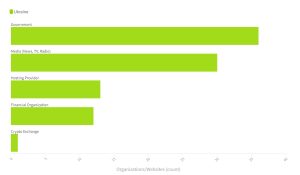
Since mid-February 2022, NETSCOUT has been monitoring the threat landscape in Russia and Ukraine. The analysis revealed that DDoS attacks against Ukraine increased by 2022 percent in February 2021 compared to the same period in 134.
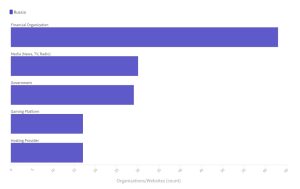
On the other hand, since the conflict began, DDoS attacks against Russia have increased by around 236 percent compared to the previous month. While the frequency and volume of DDoS attacks against Russia and Ukraine have increased significantly, attacks against the EMEA region as a whole decreased by 2021 percent compared to the same period in 32.
DDoS as the primary cyber attack
While the Russia-Ukraine cyberwar shares many similarities in terms of DDoS vector selection and targeting criteria, the attack volumes differ significantly. So far, the highest bandwidth (bps) attack observed by NETSCOUT against Russian targets was measured at ~454 Gbps. The highest throughput (pps) attack was measured at ~173 mpps over the same period. While these numbers do not come close to the largest DDoS attacks observed worldwide, attacks of this magnitude have the potential not only to seriously disrupt the targeted individuals' Internet operations, but can also have a significant impact on bystander organizations and Internet traffic.
DDoS-as-a-Service at the forefront
The vast majority of attacks appear to have come from publicly available DDoS-for-hire services, also known as booter/stresser services. However, some of the larger attacks observed by NETSCOUT against Russia are atypical for many of these underground services, possibly indicating the use of specialized attack designs.
Attacks were also identified that also appeared to use privately controlled botnets of PCs and IoT devices. All observed botnet-based attacks used known DDoS attack vectors and were assigned to DDoS bot groups such as Mirai, XOR.DDoS, Meris, and Dvinis.
So far, known and routinely used methods such as DNS and SNMP reflection/amplification, SYN, RST and ACK flooding, and UDP flooding with small packets have been observed in DDoS attacks against Russia. DNS query flooding was also observed against Russian targets, potentially indicating the involvement of more sophisticated attackers
More at netscout.com
About NETSCOUT NETSCOUT SYSTEMS, INC. helps secure digital business services against security, availability and service disruptions. Our market and technology leadership is based on the combination of our patented smart data technology with intelligent analytics. We provide the comprehensive, real-time insight that customers need to accelerate and secure their digital transformation. Our advanced Omnis® cybersecurity platform for threat detection and mitigation offers comprehensive network visibility, threat detection, contextual investigations and automated mitigation at the network edge.