
Cyber crime remains one of the greatest threats worldwide: In the new Cyber Threat Report Edition 2021/2022, the email cloud security and backup provider Hornetsecurity publishes the latest insights and data on the current threat situation with a focus on email communication, the main vector of attack .
Among other things, the report provides insights into the development of spam and advanced threats, shows which sectors are currently most threatened and identifies the methods most frequently used in cyber attacks. In addition, the "threat highlights" of the past year are highlighted.
40 percent of all inbound emails contain threats
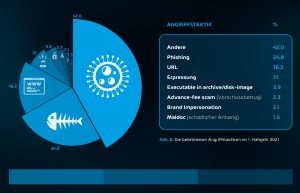
Cyber Threat Report: The most popular attack tactics in the first half of 1 (Image: Hornetsecurity).
As the main means of communication for companies, e-mail is one of the main gateways for cybercrime. The threat researchers at the Hornetsecurity Security Labs determined that 40% of all incoming emails of all email traffic in the study period represented a potential threat. This primarily includes spam, phishing e-mails and advanced threats such as CEO fraud and all types of malware. Phishing, malicious links and ransomware are among the most popular attack tactics used by hackers. Brand impersonation is particularly popular. To do this, cyber criminals copy the corporate design of the impersonated company and name the sender address in such a way that it can hardly be distinguished from the original e-mail address. The main aim is to get access to the user's access data or to spread malware via hidden links. With 16,5%, Deutsche Post and DHL are among the top 5 most frequently imitated brands.
Ransomleaks: Trend is taking on greater proportions
Almost two years ago, still in its infancy, ransom leaks are now widespread. These represent an extension of the previously known attacks with ransomware: In ransomleak attacks, the sensitive data of those affected is first copied and then encrypted. However, if payment of the ransom for decryption is refused, the cyber criminals threaten to publish the copied data on so-called leak websites.
Around 140 pieces of data were published on the REvil ransomware leak website, and new ones are added almost every day. However, this puts the hacker group “only” in 5th place among the leak websites with the most published data on ransom leak victims. In addition to these and other insights into the current situation in global cybercrime, the Cyber Threat Report Edition 2021/2022 also provides an outlook on further possible developments. The Cyber Threat Report Edition 2021/2022 with data, figures and graphics is available for download online.
More at Hornetsecurity.com
About Hornetsecurity Hornetsecurity is the leading German cloud security provider for e-mail in Europe and protects the IT infrastructure, digital communication and data of companies and organizations of all sizes. The security specialist from Hanover provides its services via 10 redundantly secured data centers around the world. The product portfolio includes all important areas of e-mail security, from spam and virus filters to legally compliant archiving and encryption, to defense against CEO fraud and ransomware. Hornetsecurity has around 200 employees at 12 locations around the world and operates with its international dealer network in more than 30 countries.
