Malwarebytes has compiled a report on ransomware for May 2022. Conti, LockBit & Co. are also there. Unfortunately, newcomers such as BlackBasta and ALPHV are also becoming more and more successful with their attacks.
With 73 ransomware attacks, LockBit was by far the most widespread ransomware in May 2022 according to the analysis of the Malwarebytes Threat Intelligence Team. This was followed by Black Basta with 22 attacks, ALPHV with 15 attacks, Hive with 14 attacks and Mindware with 13 attacks. Conti, on the other hand, only came sixth in May – Malwarebytes attributed 12 attacks to the ransomware group in its analysis. The activity was significantly lower compared to the previous month (43 attacks).
Conti overtaken - still not good news
It is striking that three of the four groups that overtook Conti in May are related to the dissolution of Conti that is currently being discussed: Black Basta, ALPHV and Hive. For example, Hive was cited as the ransomware used in the May 31st attack on Costa Rica's National Health Service.
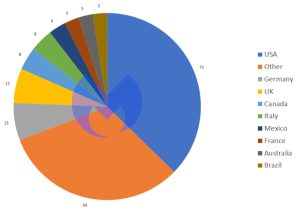
Looking at the distribution of ransomware attacks by country, in May 2022 the USA was by far the most affected country: Malwarebytes associates 75 attacks with the United States. 13 attacks can be attributed to Germany, closely followed by the UK with 12 attacks.
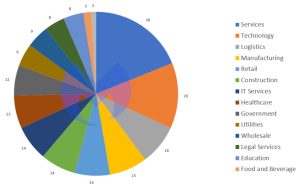
As far as industries are concerned, the service sector was particularly affected in May: According to Malwarebytes, this sector accounted for 38 attacks. In second place is technology with 26 attacks, followed by logistics with 16 attacks.
Conti: Ransomware group repeatedly attracts attention
Although only 2022 attacks were attributed to Conti in May 12, the ransomware group attracted the most attention in the last month. Conti is one of the largest and most dangerous ransomware groups. She has been involved in hundreds of attacks. Speculations are currently circulating that the group will disband and its members will reorganize. The Malwarebytes Threat Intelligence Team was able to confirm that there was an internal announcement for Conti members about the dissolution and that the group's internal chat servers are no longer accessible. The group's leak website, on the other hand, is still operational and updated with data almost daily.
More recently, Conti has indeed had some issues to deal with: On February 27, a person with access to the group's internal workings began releasing a record containing source code, files, and numerous internal chat messages. This process became known as "Conti-Leaks". A short time later, another hacker group began using the leaked source code to attack targets in Russia, breaking one of the unspoken ransomware rules.
In early May, the FBI finally put a $10 million bounty on the Conti Group's head. On May 8, Costa Rica's president declared a national emergency for the country's public sector in response to the ongoing impact of a Conti ransomware attack in April. Conti had previously published 672 gigabytes of stolen data from the Costa Rican government on the dark web.
Costa Rica attack just for show?
It would therefore be assumed that Conti is still doing quite well. According to an analysis by Advintel, however, the attacks on Costa Rica were probably a deliberate show by an organization that currently only works with emergency staff. It seems that Conti's decision to give "full support" to the Russian government in February after invading Ukraine could have been a fatal mistake. By aligning itself with the Russian state, the group made ransom payments a potential sanctions breach. This wiped out the group's earnings. As a result, according to Advintel, Conti founded sub-divisions – such as Black Basta – which should now be established before Conti disappears.
More at malwarebytes.com
Via Malwarebytes Malwarebytes protects home users and businesses from dangerous threats, ransomware and exploits that are undetected by antivirus programs. Malwarebytes completely replaces other antivirus solutions in order to avert modern cybersecurity threats for private users and companies. More than 60.000 companies and millions of users trust Malwarebyte's innovative machine learning solutions and its security researchers to avert emerging threats and eliminate malware that antiquated security solutions fail to detect. You can find more information at www.malwarebytes.com.