
Ivanti study among CISOs: Passwords are increasingly unsuitable for protecting corporate data. Remote working has accelerated the erosion of the traditional network perimeter, creating new IT security challenges for CISOs.
The Corona-related “Everywhere Enterprise” has shifted the priorities of the CISOs: reducing mobile security risks has replaced combating network security threats as a top priority. This is the result of a current survey by Ivanti among those responsible for information security in companies. Nearly nine in ten (87%) of the Chief Information Security Officers (CISO) surveyed agreed that mobile devices have become the focus of their cybersecurity strategies. Four in five (80%) CISOs said passwords are no longer an effective way to protect corporate data as hackers increasingly target external employees and mobile devices.
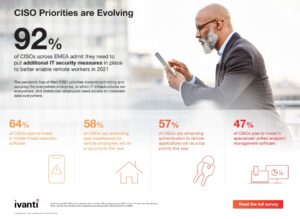
Study with 400 CISOs from the EMEA region
The study, which polled 400 CISOs in the EMEA region, found that 82 percent of respondents believe remote working is accelerating the decline of the traditional network perimeter. For CISOs, the most important thing is that only trustworthy users, devices, networks and apps can access company data:
- Access to company resources over unsecured Wi-Fi in the home offices of employees is one of the biggest vulnerabilities for IT security during the pandemic for one in two (45%) of the respondents.
- Using your own devices is an additional challenge for 40 percent of CISOs.
- Unauthorized apps pose a significant risk for a third (33%) of those surveyed.
Home office requires additional security
“The pandemic is acting as a catalyst for CISOs to ensure that working from anywhere, on any device, is just as secure as working in the office on a company-owned laptop,” said Peter Machat, vice president Central EMEA at Ivanti. “The 'everywhere enterprise' – where IT infrastructures are distributed and employees need anywhere access to company data – has dramatically changed the role of the CISO and put mobile security at the forefront. CISOs must now place a greater focus on establishing, securing and optimizing mobile work environments.”
Ivanti recommends implementing a zero trust security strategy to ensure that only trusted users can access corporate data.
Identify endpoints across the enterprise
Automation technologies also have the potential to identify, manage, secure, and maintain all endpoints, devices, and data across the enterprise. It should always be assumed that corporate networks have already been compromised. Automation technologies offer the potential to proactively detect threats and secure devices. Systems with suitable authentication - without passwords - further reduce the attack surface.
Directly to the report at ivanti.com
About Ivanti The strength of unified IT. Ivanti connects IT with security operations in the company in order to better control and secure the digital workplace. We identify IT assets on PCs, mobile devices, virtualized infrastructures or in the data center - regardless of whether they are hidden on-premise or in the cloud. Ivanti improves the provision of IT services and reduces risks in the company on the basis of specialist knowledge and automated processes. By using modern technologies in the warehouse and across the entire supply chain, Ivanti helps companies improve their ability to deliver - without changing the backend systems.
