
The problem of unused and forgotten tools - chronology of a Midas ransomware attack. The Sophos Rapid Response Team describes how cybercriminals proceeded in a real Midas attack case and how they moved in the network via commercial tools from October to December 2021 before finally launching the ransomware attack.
With an integrated security ecosystem and Zero Trust, attackers would have had little chance of infiltrating the network and the attacked organization would have had greater control over unauthorized network access.
Major attack with Midas ransomware
After a ransomware attack on a technology provider in December 2021 the Sophos Rapid Response team was called to help. Forensic findings show that at least two different commercial remote access tools and an open-source Windows utility were used in the attack using the lesser-known Midas ransomware. During their analysis, the experts also discovered evidence that the cybercriminals were active on a domain controller and other computers in the network at least two months before the ransomware appeared. This corresponds to a classic chain of events that could probably have been prevented with a consistent security strategy and zero trust.
A typical IT structure harbors risks
The attacked company operated an IT and security infrastructure of the kind that can be found thousands of times over. Citrix was used to virtualize the employee desktops. The network topology was organized flat, with the entire network accessible through the VPN. Most of the physical devices consisted of Windows servers running virtual machines. There was no segmentation of the network. All in all, a typical infrastructure that makes a cyber attack comparatively easy.
course of the attack
The attack was carried out with multiple actions by the threat actors, creating Windows services to run multiple PowerShell scripts on one machine at a time, which in turn involved other machines in their attack along the way. This enabled them to access any other machine, regardless of whether it was a server or a VM, via the SMB protocol.
In a Zero Trust environment, properly configured access controls could have prevented attackers from using one compromised computer against another.
In retrospect, the forensics were able to date what is presumably the first compromise to 13 October. It was not until December 7th that the attackers began distributing the ransomware binary to the computers in the network. As a result, the intruders went unnoticed for over two months. They executed commands, started internal RDP connections, used commercial remote access software already installed, exfiltrated data to the cloud, and moved files to and from one of the target's domain controllers.
The problem of unused and forgotten tools
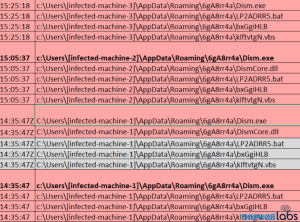
Repeated commands run on multiple computers over the course of an hour set up services that sideloaded the malicious DismCore.dll on startup (Image: Sophos).
While Midas is not a prominent threat like some of the other ransomware families, the attackers seemed to be following a familiar pattern throughout the incident. They used traditional Windows management tools and processes (e.g. PowerShell and the Deployment Image Servicing and Management Tool) as well as commercial remote access tools (AnyDesk and TeamViewer) which are less likely to trigger an anti-malware alert .
In this incident, the company's IT team tested AnyDesk, TeamViewer, as well as various other remote access tools. Although the tools were ultimately not used, they remain unused on various servers, which cybercriminals use to their advantage. In some cases, they also used the open-source Process Hacker tool to identify and bypass the endpoint security products used by the attacked company.
A security ecosystem with Zero Trust would have protected
“This is a good example of what can happen to many companies because they run their IT in one way or another. Shielding company networks mainly from the outside is certainly an effective protection method in connection with an integrated security ecosystem. However, even this perimeter-based approach has more and more gaps. Employees are increasingly working on the go, also via other networks. There are also software-as-a-service applications (SaaS), cloud platforms and cloud-based services. There is hardly any corporate network in which all the systems integrated in it are secure. This is where the Zero Trust concept – trusting nothing and nobody and checking everything – comes into play,” says Michael Veit, security expert at Sophos.
More at Sophos.com
About Sophos More than 100 million users in 150 countries trust Sophos. We offer the best protection against complex IT threats and data loss. Our comprehensive security solutions are easy to deploy, use and manage. They offer the lowest total cost of ownership in the industry. Sophos offers award-winning encryption solutions, security solutions for endpoints, networks, mobile devices, email and the web. In addition, there is support from SophosLabs, our worldwide network of our own analysis centers. The Sophos headquarters are in Boston, USA and Oxford, UK.
