Online banking trojan group Trickbot remains active. Analyzes show that new VNC modules with additional functions are being developed for the botnet. A technical report by Bogdan Botezatu, Director of Threat Research & Reporting at Bitdefender.
Trickbot malware and its associated botnet have been active since it was first discovered in 2016. The attacker group behind it has managed to infect several million PCs worldwide during this time. The Trickbot actors who emerged from the Dyre malware environment have built a veritable ecosystem of plug-in modules and additional components and are continuously working on new functionalities: The experts are currently monitoring the further development of Virtual Network Computing (VNC) Module vncDII. Attackers can access extensive information on infected computers via alternative desktops and reload new malicious functions.
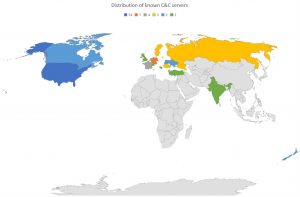
The latest analyzes by Bitdefender Labs show that the Trickbot group is working on its botnet with great energy despite increasing pressure from law enforcement agencies. The cybercriminal gang, which operates from Russia, Belarus, Ukraine and Suriname, is continuously developing its command-and-control server infrastructure. Of the 71 command and control servers identified, 54 are currently located in the USA, seven in Germany and three in France.
Contact the command center
The current Virtual Network Computing (VNC) module tvncDll from Trickbot malware offers new functions for monitoring the attacked systems and collecting information. tvncDll is an update to the vncDll module that the group used to attack selected prominent targets. A very high frequency of updates and bug fixes shows how intensively the criminal developers are working on the system.
tvncDlI uses its own communication protocol that obscures which data the module transmits to the command and control (C2) server without the knowledge of the victim.
Shortly after the successful infection
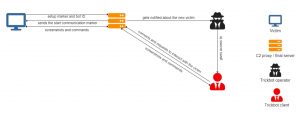
After a successful infection, the C2 server sends the configuration file vnconf to the module via the control function and the SetConf command. This configuration file contains up to nine IP addresses of predefined C2 servers. The servers act as links between the victim and the attacker and currently enable the hackers to access the systems of victims behind a firewall.
In the course of the setup, the client module first informs the first available C2 server of its existence by sending a marker and waits for further commands. It also sends the bot ID, which uniquely identifies the module implemented on the computer.
Depending on the response from the server
- the module either remains inactive and waits for a signal from the C2 server to take action,
- it ends its activity and asks Trickbot to delete the module from its memory, or
- it goes into operating mode. This starts the exchange of messages between the client and the malicious host. In full duplex, the victim system transmits screenshots of the alternative desktop and clipboard information.
The data traffic with the C2 servers runs via port 443 in order to generate less suspicion. While the traffic on this port usually runs over SSL or TLS, the cyber criminals send the data unencrypted.
Alternative desktop under the control of the module
The module creates its own alternative desktop that the attacker controls completely via the module (Fig. 4). The intruders can perform several actions using PowerShell via the menu item Cmd.exe. This includes:
- downloading new payloads to carry out attacks within the network,
- opening various documents or the e-mail inbox,
- as well as uploading the data and information from the victim computer to the command and control server.
The "Native Browser" button enables the disclosure of passwords in password dumps. The development of this feature is in full swing, as evidenced by several weekly updates. A left-click on "Native Browser" shows your own browser with the option of dumping the access data via Internet Explorer (Fig. 5). Obviously, thought has been given to providing this option under Chrome, Firefox and Opera. The buttons for this have been created.
Complex infrastructures in the background
These analyzes show how cybercriminal attackers are constantly improving their attack methods and building complex Trickbot infrastructures and increasing their potential for danger. The complete analysis of the new developments for Trickbot by the experts at Bitdefender Labs can also be found online at Bitdefender.
More at Bitdefender.com
About Bitdefender Bitdefender is a leading global provider of cybersecurity solutions and antivirus software, protecting over 500 million systems in more than 150 countries. Since it was founded in 2001, the company's innovations have consistently ensured excellent security products and intelligent protection for devices, networks and cloud services for private customers and companies. As the supplier of choice, Bitdefender technology is found in 38 percent of security solutions deployed around the world and is trusted and recognized by industry experts, manufacturers and customers alike. www.bitdefender.de