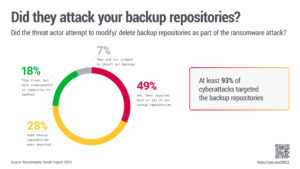
Veeam's 2023 Ransomware Trends Report shows that 93 percent of all cyber attacks target backup storage to force ransom payments. Cyber insurance is becoming too expensive and 21 percent of organizations cannot recover their data after paying the ransom.
Businesses of all sizes are increasingly falling victim to ransomware attacks and are inadequately protecting themselves against this growing cyber threat. According to new data from the 2023 Veeam® Ransomware Trends Report, one in seven organizations will have almost all their data (>80%) affected by a ransomware attack, indicating a significant protection gap. Veeam Software found that cyber criminals almost always (more than 93 percent) target backups during cyber attacks and manage to compromise their victims' ability to recover 75 percent of the time. This underscores the importance of immutability and air-gapping to ensure backup repositories are protected.
Decrease victims' ability to recover
The 2023 Veeam Ransomware Trends Report includes insights from 1200 affected organizations from nearly 3000 cyberattacks, making it one of the most comprehensive reports of its kind. The study examines the key insights from these incidents, their impact on IT environments, and which ones were taken or needed Steps to implement data backup strategies that ensure business resilience. The report looks at four different roles involved in cyber security and/or cyber defenses: security professionals, CISOs or similar IT leadership roles, IT operations generalists, and backup administrators.
“The report shows that today it is no longer a question of when a company becomes the target of a cyber attack, but of how often. While safety and prevention are still important, it is critical that any business focus on how quickly they can recover by making their organization more resilient,” said Danny Allan, CTO at Veeam. “We need to focus on effective ransomware prevention by going back to basics, that is strong security measures and testing of original data and backups. Both the continued existence of the backup solutions and the coordination between the backup and cyber teams must be ensured in order to achieve a uniform attitude within the company.”
Ransom payment: no guarantee of data recovery
For the second year in a row, the majority (80 percent) of organizations surveyed have paid a ransom to stop an attack and recover data -- a 4 percent increase year-over-year -- despite 41 percent of organizations accepting a do-not-pay -Have a ransomware policy. But while 59 percent paid the ransom and were then able to recover their data, 21 percent still didn't get their data back from the cybercriminals. Unfortunately, the number of companies that were able to recover their data themselves without paying a ransom has fallen from 19 percent in last year's survey to 16 percent now.
Only protected backups are a trump card
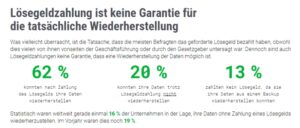
🔎 A lot of ransom for nothing? This was the case for almost 40 percent of the victims (Image: Veem).
After a ransomware attack, IT managers have two options: pay the ransom or restore from backup. In terms of recovery, the study shows that in almost all cyber incidents (93 percent), criminals attempt to attack the backup repositories. As a result, 75 percent of organizations lose at least a portion of their backup repositories during the attack, and more than a third (39 percent) of backup repositories are lost entirely.
By attacking the backup solution, attackers eliminate the possibility of recovery and force ransom payments. Best practices—such as securing backup credentials, automating cyber-detection scans of backups, and automatically checking backup recoverability—are important to protect against attacks.
However, the most important tactic is to ensure that the backup repositories cannot be deleted or corrupted. To that end, organizations need to focus on immutability. The good news is that 82 percent of organizations are using immutable cloud and 64 percent are using immutable disk, while only 2 percent of organizations are not using immutability on at least one tier of their backup solution.
No reinfection during recovery
When asked how they ensure data is “clean” upon recovery, 44 percent of respondents said they perform some form of isolated staging to re-validate data from backup repositories before bringing it back to production. However, this means that the majority (56 percent) of companies risk reinfecting the production environment because they have no way of ensuring their data is "clean" during recovery. For this reason, this exam is very important.
Key takeaways from the 2023 Veeam Ransomware Trends Report
- Cyber insurance is becoming too expensive: 21 percent of companies said ransomware is now specifically excluded from their policies, and those who purchased cyber insurance saw significant changes at their last policy renewal: 74 percent got higher premiums, 43 percent got a higher deductible, and 10 percent reduction in insurance benefits.
- Incident response guidelines depend on backup: 87 percent of organizations have a risk management program that drives their security plan, yet only 35 percent feel their program is working well. 52 percent are trying to improve their situation, with 13 percent not yet having a program. The results show that the most common elements of the cyber attack preparedness guide are clean backup copies and periodic backup recoverability checks.
- Organizational alignment continues to suffer: Although many companies view ransomware as a disaster and therefore incorporate cyber attacks into their business continuity or disaster recovery (BC/DR) planning, 60 percent of companies say they are still significantly improving their backup and cyber team formations or need to be completely overhauled to be prepared for this scenario.
The background to the report
Veeam commissioned independent market research firm Vanson Bourne to conduct a survey of 1200 unbiased IT executives on the impact of ransomware in their environments, as well as their future IT strategies and privacy initiatives. All respondents were affected by at least one successful cyberattack in 2022. Respondents represented organizations of all sizes from 14 different countries across APJ, EMEA and the Americas.
More at Veeam.com
About Veeam Veeam offers companies resiliency through data security, data recovery and data freedom for their hybrid cloud. Veeam Data Platform offers a single solution for cloud, virtual, physical, SaaS and Kubernetes environments, giving businesses the confidence that their applications and data are protected and always available to keep their businesses running.