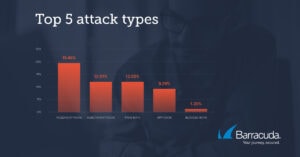
New Barracuda investigation: Cyber criminals are increasingly turning to bots and automation to make their attacks more efficient and to avoid detection. Barracuda analyzed a two-month data sample of web application attacks that were blocked by Barracuda systems and found a massive number of automated attacks. The top five attacks were dominated by attacks carried out with automated tools.
Almost 20 percent of the attacks discovered were fuzzing attacks in which automation attempts to find and exploit application vulnerabilities. Injection attacks followed with around 12 percent, with most attackers using automated tools such as sqlmap to break into the applications. Many of these attacks were script-kiddie-level attacks, with no exploration taking place to individualize the attacks. Bots pretending to be Google bots or similar were just behind with a little more than 12 percent of the attacks on web applications analyzed. DDoS attacks on applications (Distributed Denial of Service) were surprisingly widespread and made up more than 9 percent of the sample analyzed. A small fraction of the attacks (1,2 percent) came from bots that were blocked by site administrators.
Here's a closer look at the trends in web app attacks and the ways cybercriminals use automated attacks.
Current trends in web app attacks
Automated attacks use bots to exploit vulnerabilities in web applications. These attacks can range from fake bots posing as Google bots to avoid detection, to DDoS attacks on applications that attempt to crash a website by subtly overloading the application.
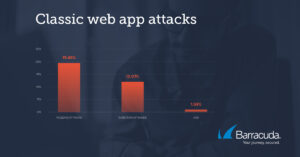
While bot traffic is a rapidly growing problem, it doesn't mean cyber criminals are abandoning their old ways. The majority of the attacks analyzed by Barracuda were classic web app attacks such as injection attacks (12 percent) and cross-site scripting (XSS) (1 percent). As mentioned, most of the attack traffic comes from intelligence tools or fuzzing tools used to probe applications.
Often used: injection attacks
Injection attacks are currently the top attack in the OWASP Top 10, a list of the most critical security risks, and have been featured in every issue since the first list. There is no sign that these attacks will go away as they are relatively easy to execute and can generate huge profits for cyber criminals. Cross-site scripting attacks were also very popular and ranked third among the most common attacks in this category.
A significant part of the attack traffic analyzed targeted WordPress or PHP vulnerabilities (typically the phpMyAdmin pages), namely 6,1 percent and 1,05 percent, respectively. However, some of these attacks were also directed against non-PHP or non-WP sites, suggesting that some attackers are script kiddies. However, these attackers will likely soon learn to conduct a better exploration before launching the attacks.
Revival: Request smuggling attacks
Request smuggling attacks had declined to a negligible level in the past until the HTTP desync attacks were recently exposed. Since then, smuggling attacks have returned in a big way. Request smuggling attacks exploit the server's inability to securely deal with anomalies in various aspects of an HTTP request. Barracuda research found that more than 60 percent of smuggling attacks used an invalid header. A third used a multiple content length, 3 percent had an incorrect content length.
Attacks against JSON APIs
Most of the attacks that Barracuda observed against JSON APIs were boundary conditions tested, which means that an attempt was ultimately made to fuzz the APIs. 95 percent of these types of attacks exceeded the Max Number Value, and nearly 4 percent of these attacks exceeded the Max Value Length. The analysis also showed other traffic attack attempts (XSS and SQL injection attacks), but the volume of these types of attacks was very small to negligible in the sample. It is expected that this will increase over the next year.
Attacks aimed at data breaches have primarily focused on stealing sensitive information such as credit card numbers. Visa was the clear focus, with more than three-quarters of these attacks. JCB followed at a great distance with more than 20 percent and Mastercard, Diners and American Express with a significantly lower share.
The security status of the encryption
Encrypting traffic prevents a wide variety of attacks, such as man-in-the-middle attacks, and provides a layer of protection for users visiting websites. However, attacks can still take place within the data stream. Almost 92 percent of the analyzed data traffic ran over HTTPS. Less than 10 percent of the traffic was handled over HTTP. This is good news for the security status of web applications.
Browser vendors have prioritized TLS1.3 as the preferred protocol and this is starting to affect the general acceptance of these protocols. In the sample examined, only a few companies had activated the older, significantly insecure SSLv3 protocol. And even among the companies that enabled this protocol, there was very little SSLv3 traffic. The same goes for TLS1.0 and TLS1.1, although the use of these protocols is rapidly declining, each accounting for less than 1 percent of the traffic analyzed. A full 65 percent of the analyzed data traffic used TLS1.3, the most secure protocol currently available. About a third of HTTPS traffic is still on TLS1.2, but that number is slowly falling.
Browser analysis at TLS1.3
When we analyzed browsers using TLS1.3 (based on the reported user agent), Chrome was the most popular browser with 47 percent of traffic, followed by Safari, which accounted for 34 percent of TLS1.3 traffic. Surprisingly, Edge pushed Firefox into third place with 16 percent. Firefox was used for only 3 percent of the traffic. The fact that Firefox has lost ground to Edge is likely due to two things: Chrome's dominance and the shift from corporate systems to Edge, which previously preferred Internet Explorer.
TLS1.2 shows a rather surprising trend. Internet Explorer usage is higher than Chrome usage here, with Internet Explorer accounting for more than half of the data traffic, while Chrome usage is just under 40 percent. In comparison, Safari comes in at less than 10 percent, the use of Firefox is even lower.
User trend towards safer browsers
The investigation also showed that the automatic updates for Chrome and Firefox are used quite frequently. Most of the browser versions in the analysis were among the newest or one or two versions behind. There are still a large number of Internet Explorer users out there, but IE11 was the version that was used the vast majority of cases. This shows a trend towards more up-to-date and safer browsers. In comparison, the automated traffic used little TLS1.3; most of them use TLS1.2. This includes website monitoring, bots and tools like curl.
How companies can protect themselves from automated attacks
When it comes to protecting against newer attacks like bots and API attacks, security teams can sometimes be overwhelmed by the multitude of solutions required. The good news is that these solutions are being consolidated into WAF / WAF-as-a-Service solutions, also known as Web Application and API Protection Services (WAAP).
WAF Magic Quadrant 2020 WAAP Services
Gartner defines WAAP services as the evolution of cloud WAF services in its WAF Magic Quadrant 2020: "WAAP services combine a cloud-based as-a-service delivery of WAF, bot mitigation, DDoS protection and API Security with a subscription model. ”Organizations should therefore look for a WAF-as-a-Service or WAAP solution that includes bot mitigation, DDoS protection, API security, and credential stuffing protection and ensure that it is configured correctly.
It is also important to stay informed about current threats and their development. Barracuda predicts the top three attacks applications will face this year will be automated bot attacks, APIs attacks, and software supply chain attacks. There are fewer protective mechanisms against these newer attacks and they are more likely to be let through partly because of a lack of understanding and in some cases because of shadow applications that are provided without appropriate protective mechanisms. However, by combining specialist knowledge of the latest cybercriminal attack tactics and current technologies, companies can significantly reduce the risks of increasingly automated attacks on web applications.
More at Barracuda.com[starboxid=5]