
Attacks with Conti ransomware on Exchange servers continue - and are becoming more and more efficient. SophosLabs discovered that the cybercriminals had introduced seven backdoors in an attack.
Investigations of the latest attacks on Exchange servers with Conti ransomware have shown that the cyber criminals access the systems via ProxyShell. Various critical updates have been released over the past few months for the vulnerabilities in Microsoft Exchange. ProxyShell is an evolution of the ProxyLogon attack method. In recent months, the exploit has become one of the most important tools among ransomware attackers - including those using the new LockFile ransomware, which first appeared in July.
With increasing knowledge about this attack method, the length of time cybercriminals spend from the start to the final activation of the ransomware on the target networks has shortened from weeks to hours.
Fast "efficient" attacks
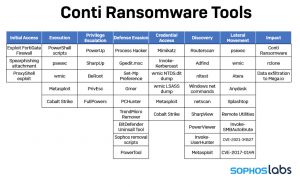
A wide range of Conti ransomware tools offer attackers a wide range of attack options (Image: Sophos).
In a ProxyShell-based attack observed by Sophos, the Conti attackers succeeded in gaining access to the victim's network in less than a minute, including setting up a remote web shell. Three minutes later, the criminals installed a second backup web shell. In just 30 minutes, they had a complete list of the computers, domain controllers, and domain administrators on the network. After four hours, the Conti attackers had the credentials of the domain administrator accounts in their hands and started executing commands. Within 48 hours of the initial access, the attackers exfiltrated around 1 terabyte of data. After five days, they released the Conti ransomware across the network, specifically targeting individual network shares on each computer.
Evil Legacy: 7 back doors
In the course of the break-in, the Conti attackers installed no fewer than seven back doors in the network: two web shells, Cobalt Strike and four commercial remote access tools (AnyDesk, Atera, Splashtop and Remote Utilities). The early installed web shells were mainly used for initial access; Cobalt Strike and AnyDesk are the primary tools they used for the remainder of the attack.
More at Sophos.com
About Sophos More than 100 million users in 150 countries trust Sophos. We offer the best protection against complex IT threats and data loss. Our comprehensive security solutions are easy to deploy, use and manage. They offer the lowest total cost of ownership in the industry. Sophos offers award-winning encryption solutions, security solutions for endpoints, networks, mobile devices, email and the web. In addition, there is support from SophosLabs, our worldwide network of our own analysis centers. The Sophos headquarters are in Boston, USA and Oxford, UK.
