
In its Clustering Attacker Behavior Reveals Hidden Patterns report, Sophos publishes new insights into connections between the most prominent ransomware groups of the past year: Hive, Black Basta and Royal. Recent attacks suggest that the three ransomware groups share playbooks or partners.
As of January 2023, Sophos X-Ops had investigated four different ransomware attacks over a three-month period, one originating from Hive, two from Royal and one from Black Basta. Clear similarities between the attacks were found.
Although Royal is considered a very closed group, not visibly involving partners from underground forums, subtle similarities in the forensics of the attacks suggest that all three groups share either partners or highly specific technical details in their activities. Sophos tracks and monitors the attacks as a "cluster of threat activity" that defenders can leverage to reduce detection and response times.
Cooperation of ransomware groups
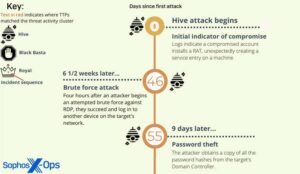
🔎 The first detection of threat activity cluster behavior was in logs collected during a Hive ransomware attack (Image: Sophos).
"In general, because the ransomware-as-a-service model requires external partners to execute the attacks, it is not uncommon for there to be overlaps in tactics, techniques and procedures (TTPs) between different ransomware groups. In these cases, however, the similarities are at a very subtle level. These highly specific behaviors suggest that the Royal ransomware group is much more dependent on partners than previously thought,” says Andrew Brandt, senior researcher at Sophos.
The specific similarities include the following three aspects in particular: First, if the attackers had taken control of the systems of the targets, the same specific usernames and passwords were used. Second, the final payload was provided in a .7z archive, each named after the victim organization. Third, commands were run on the infected systems using the same batch scripts and files.
Use of identical scripts
Sophos X-Ops was able to uncover these connections as part of an investigation into four ransomware attacks that took place over a three-month period. The first attack was in January 2023 with the Hive ransomware. This was followed by two attacks by the Royal group in February and March and finally one by Black Basta in March of this year.
A possible reason for the similarities in the observed ransomware attacks could be the fact that towards the end of January 2023, after a covert operation by the FBI, a large part of Hive's operations were dismantled. This may have led to Hive partners looking for new employment - possibly with Royal and Black Basta - which could explain the striking matches found in subsequent ransomware attacks. Because of these similarities, Sophos X-Ops began tracking all four ransomware incidents as a cluster of threat activities.
Threat Activity Clustering
“If the first steps in threat activity clustering are to map to groups, there is a risk that researchers will focus too much on the 'who' of an attack and overlook important opportunities to strengthen defenses. Knowledge of highly specific attacker behavior helps Managed Detection and Response (MDR) teams respond more quickly to active attacks. It also helps security vendors develop stronger protections for customers. And when defenses are based on behavior, it doesn't matter who attacks. Whether it's Royal, Black Basta, or others, potential victims will have the necessary safeguards in place to block attacks that share some of the distinctive characteristics,” says Brandt. So far this year, Royal ransomware is the second most common ransomware family detected by Sophos Incident Response.
More at Sophos.com
About Sophos More than 100 million users in 150 countries trust Sophos. We offer the best protection against complex IT threats and data loss. Our comprehensive security solutions are easy to deploy, use and manage. They offer the lowest total cost of ownership in the industry. Sophos offers award-winning encryption solutions, security solutions for endpoints, networks, mobile devices, email and the web. In addition, there is support from SophosLabs, our worldwide network of our own analysis centers. The Sophos headquarters are in Boston, USA and Oxford, UK.
