
Last year, Germany was the fourth most attacked country in the world. The logistics, construction and technology industries are the main targets, according to Malwarebytes ransomware analysis.
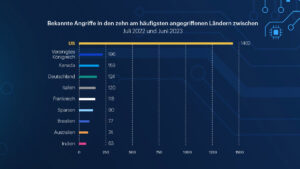
🔎Known ransomware attacks in the top ten most attacked countries, July 2022 to June 2023. (Image: Malwarebytes)
In the twelve months from July 2022 to June 2023, Germany remains the fourth most attacked country in the world and the most attacked country outside the English-speaking world.
Ransomware attacks are increasing
As in the US and UK, the number of ransomware attacks has increased significantly over the past four months. March, April and May were even the most affected months during the observation period. There were 24 known attacks in Germany in May. This made it the worst affected month of the past year - with almost three times as many attacks as the average for the previous eleven months.
Although some of the increase is due to a small increase in the number of ransomware groups operating in Germany, the main cause appears to be an increase in activity from groups that were already active. Five different gangs were responsible for more than one attack in both May and June 2023.
In Germany, the logistics, construction and technology sectors are particularly affected
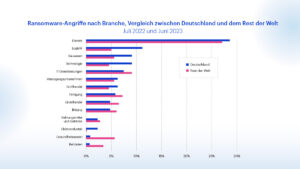
🔎Ransomware attacks in Germany by industry compared to the rest of the world, July 2022 to June 2023. (Image: Malwarebytes)
The service sector was the most affected in Germany in the past twelve months, accounting for 29 percent of all known attacks. This is roughly in line with the global average and the picture in other major ransomware destinations such as the US, UK and France.
What is also striking in Germany is that Germany appears to have been spared the targeted focus on education, as has been observed in the USA and the UK, especially in the last twelve months. The healthcare sector was also not a significant target, unlike the US, and the public sector was also spared the attention of attackers in neighboring France.
However, a comparison between Germany and the rest of the world shows that certain sectors were proportionally more affected in Germany than elsewhere: especially logistics, construction and technology. The ransomware groups in Germany seem to concentrate entirely on companies.
Exploiting Zero Days: New Ransomware Tactics Coming?
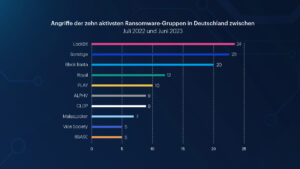
🔎Attacks in Germany by the ten most active ransomware groups, July 2022 to June 2023. (Image: Malwarebytes)
In the past twelve months, Malwarebytes has discovered 23 ransomware groups operating in Germany. Nine of them were responsible for five or more known attacks, including the group known as Cl0P.
LockBit has been the most active group in Germany over the past twelve months, as well as in the USA, the UK and France. Black Basta was the second most active group in Germany in the past twelve months (after the USA). This continued the trend of Black Basta concentrating primarily on Germany. Malwarebytes first reported on this in April. Black Basta committed twice as many attacks in Germany as in the United Kingdom or Canada, while she reported only one attack in France.
The presence of Cl0P and MalasLocker in the top ten is also telling and could be an indication of a change in ransomware tactics and a possible escalation of the ransomware problem. MalasLocker's attacks all occurred in a single month, May. Cl0P has only been active in four of the last 12 months and has seen half of its known attacks in just a single month as well. Nevertheless, both groups were among the most productive groups in Germany last year. They achieved this through campaigns that targeted specific, unpatched vulnerabilities. MalasLocker exploited a vulnerability in Zimbra servers to emerge out of nowhere in May as the most widespread ransomware in Germany and worldwide. Cl0P used a similar tactic by exploiting zero-days in GoAnywhere and MOVEit Transfer.
New attack tactics are quickly emerging
It is a feature of the ransomware ecosystem that when one group discovers a new and successful tactic, other groups quickly follow suit. The last major change came in 2019, when ransomware group Maze triggered a wholesale shift to so-called “double extortion,” which uses both encryption and the threat of data leaks to extort victims. The use of zero days at Cl0P has the potential to bring about a similar change. Whether this is the case will ultimately depend on the return on investment of the tactic.
Marcelo Rivero, ransomware specialist at Malwarebytes, sees Cl0P's latest campaign as only a partial success for the group: “From Cl0P's perspective, the campaign was a mixed success. Although a previously unknown vulnerability was exploited, the generally low quality of the stolen data may not have satisfied the group.”
The Cl0P campaigns in 2023 have shown that ransomware gangs can now handle the cost and complexity of deploying zero-days. And when they do, the volume of attacks can go far beyond what was previously possible with other approaches.
Go directly to the report at Malwarebytes.com
Via Malwarebytes Malwarebytes protects home users and businesses from dangerous threats, ransomware and exploits that are undetected by antivirus programs. Malwarebytes completely replaces other antivirus solutions in order to avert modern cybersecurity threats for private users and companies. More than 60.000 companies and millions of users trust Malwarebyte's innovative machine learning solutions and its security researchers to avert emerging threats and eliminate malware that antiquated security solutions fail to detect. You can find more information at www.malwarebytes.com.
Matching articles on the topic
