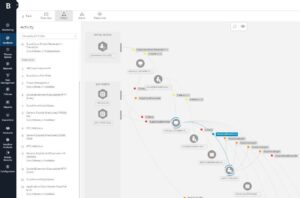
More and more companies are moving digital assets to the cloud. As a result, the IT attack surface is expanding and, intensified by the multi-cloud, is becoming increasingly complex. Cloud Security Posture Management, or CSPM for short, checks cloud environments and notifies the responsible specialists about configuration vulnerabilities.
Attack surfaces are dynamic and their number is continually increasing. Due to digital transformation and hybrid, locally flexible working, an enormously growing number of devices, web applications, software-as-a-service platforms (SaaS) and other third-party services require connection to the corporate network.
Team: Cloud Security Posture Management
At the same time, companies are moving more and more business-critical systems to the cloud and distributing them across multiple cloud service providers (CSPs) and in data centers. Cloud Security Posture Management (CSPM) is becoming a top priority in more and more organizations. The basic tasks of cloud security are comparable to the security setup in the traditional IT of a local data center.
As processes shift to digitization and moving to the cloud, IT security managers need comprehensive visibility into emerging attack surfaces. Especially in multi-cloud, they demand tools for consistent security control regardless of the underlying infrastructure.
Cloud demands good security
Compared to traditional data center architectures, the importance of protecting against attack mechanisms that apply equally to cloud and on-premise IT remains. What has changed in the cloud is the underlying infrastructure and authorized entities' access to digital resources.
One result of the trend of moving business-critical systems to the cloud and multi-cloud is the increased complexity of IT. Monitoring the IT security situation has become more difficult. At the same time, paradoxically, the core benefit of the cloud – setting up, configuring and scaling infrastructure as needed – makes it easier for attackers to detect vulnerabilities in order to gain access to instances in the multi-cloud.
Limits of conventional IT security
Traditional cybersecurity solutions are ill-equipped to protect the dynamic attack surfaces that emerge in the multi-cloud. They are still designed for static IT, where applications run in a hardened data center and only a manageable number of users from outside the network have a legitimate reason for requesting access. Therefore, they cannot keep pace with the increasing complexity and flexibility of today's IT structures.
In the new confusion, cybercriminals can simultaneously disguise their communication attempts as legitimate data traffic and hide their evasive maneuvers in the growing volume of authorization requests. For example, attackers constantly scan cloud IPs to find misconfigurations, overprivileged identities, and outdated, inadequate authentication mechanisms. Additionally, many cybercriminals can download a list of open S3 buckets or search for private API keys on GitHub to find access to data or the network.
New security status thanks to Cloud Security Posture Management (CSPM)
CSPM can help companies better manage these problems. Here are five key tasks that a cloud security overhaul should accomplish:
1. See the digital landscape in its entirety
No one can protect what they cannot see. IT security teams therefore need complete visibility of the attack surface - from on-premises infrastructure and managed assets to multi-cloud and third-party web applications to remote endpoints. CSPM provides comprehensive insight into a company's cloud landscape. In order to optimally utilize the information gained, it should be seamlessly integrated into its entire digital infrastructure. Ideally, this is done on a comprehensive platform that covers both the cloud and all other digital assets.
2. Thoroughly enforce safety standards
To implement recommended security standards in multi-cloud structures, it is important to identify gaps in defenses. A CSPM must answer several questions. Is the configuration correct? Does every endpoint have an anti-malware program? Is the data encrypted according to recognized standards? A CSPM only fulfills its tasks if it provides IT security officers with the means to implement and enforce basic security guidelines. In the next step, you can put additional industry or company-specific guidelines and regulations on the agenda that are mandatory or useful for the company.
3. Manage identities and access rights easily and transparently
A CSPM as a comprehensive tool for establishing IT security provides an overview of guidelines for identity and access management in the multi-cloud. Enterprises use an enormous number of cloud services, from storage to load balancing, and it is almost impossible to know which entity is accessing which asset and why. It is not uncommon for policies or machine identities with privileged rights to still be in effect and thus provide access that no one needs anymore or that the IT administrator has long since forgotten. In addition, many administrators, driven by the need for productivity, retreat to standards of authorization policies. The end result is that they give web services and other entities far more access rights than necessary. Solid access management is therefore fundamental to the least-privilege cyber hygiene that is essential, especially in complex circumstances.
4. Detect and close security gaps efficiently
Securing an ever-growing attack surface depends on the ability to prioritize problems. No team of security analysts, no matter how large, can keep up with the current increase in network surface area in dynamic multi-cloud infrastructures. There is no way around machine scaling to cover all areas and escalate the most critical vulnerabilities. Effective CSPM prioritizes problems in a largely automated way. It recommends ways to remediate vulnerabilities that are highly automated on the one hand and that the administrator can monitor on the other. It evaluates risks in accordance with the company's goals.
5. Easy to implement
Above all, CSPM must reduce complexity. Security teams should be able to quickly implement a CSPM and immediately gain comprehensive insight into their attack surface. The platform should provide actionable insights and actionable recommendations to resolve the most critical vulnerabilities as quickly as possible. This makes it a valuable resource even if the security team has little knowledge of cloud security.
Capture the cloud
Constantly new attack surfaces are changing today's threat landscape and giving attackers ample opportunity to detect and exploit vulnerabilities in security defenses. Conventional IT security is unable to close these gaps. CSPM helps organizations better manage their growing attack surfaces by providing visibility into the cloud landscape and assessing emerging risks. It provides the opportunity to harden cloud structures. With automated processes, it implements protection in complex landscapes even with limited know-how and resources. Simply implemented, a CSPM quickly becomes effective.
More at Bitdefender.com
About Bitdefender Bitdefender is a leading global provider of cybersecurity solutions and antivirus software, protecting over 500 million systems in more than 150 countries. Since it was founded in 2001, the company's innovations have consistently ensured excellent security products and intelligent protection for devices, networks and cloud services for private customers and companies. As the supplier of choice, Bitdefender technology is found in 38 percent of security solutions deployed around the world and is trusted and recognized by industry experts, manufacturers and customers alike. www.bitdefender.de