Bitdefender Labs uncovered and analyzed a complex industrial espionage attack. The most likely originator of the campaign was the advanced persistent threat (APT) group Backdoor Diplomacy, which has ties to China.
The victims are currently found in the telecommunications industry in the Middle East. The actions of the cyber criminals started in August 2021. The campaign was designed in several phases and used a web shell in an email attachment to gain initial access to the victim system. The subject and attachment of the emails indicated that an Exchange server was the infection vector.
In search of more control
In search of information, the attackers used built-in utility tools such as hostname.exe, systeminfo.exe, ipconfig.exe, netstat.exe, ping.exe and net.exe. They were looking for information about the configuration of PC systems, domain controllers and computers and users, but also about specific groups such as domain administrators or remote desktop users. Using tools like Ldifde and csvde, they exported data from Active Directory. Open source scanners and other publicly available software such as Nimscan, SoftPErfect Network Scanner v5.4.8 Network Service Management Tool – v2.1.0.0 and Netbios Scanner were also used.
With mechanisms such as registration keys and services, as well as a subscription to Windows Management Instrumentation (WMI), the cybercriminals gained a persistent presence in the victim network. In order to camouflage themselves from the cyber defense, the perpetrators of the attack used different loaders, escalated existing privileges of digital identities, excluded paths for a malware scan and manipulated time stamps. Powershell commands and keyloggers were used to spy on emails, including metadata. Generally, the attackers used a variety of legitimate or even custom tools.
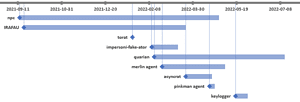
Extensive tool box
The hackers used a whole arsenal of tools such as the IRAFAU backdoor - later replaced by Quarian - for downloading and uploading and manipulating files - and Remote Shell. Pinkman Agent and a tool discovered by Bitdefender experts and named "Impersoni-fake-ator" to prevent the defense from detecting the malicious purposes. Legitimate tools like DbgView and Putty also cloaked the malicious processes. There were other tools for remote access, proxying and tunneling of data. A timeline shows how the attackers used the various tools for their campaign one after the other.
More at Bitdefender.com
About Bitdefender Bitdefender is a leading global provider of cybersecurity solutions and antivirus software, protecting over 500 million systems in more than 150 countries. Since it was founded in 2001, the company's innovations have consistently ensured excellent security products and intelligent protection for devices, networks and cloud services for private customers and companies. As the supplier of choice, Bitdefender technology is found in 38 percent of security solutions deployed around the world and is trusted and recognized by industry experts, manufacturers and customers alike. www.bitdefender.de