
Cybercriminals stole the credit card details, personal information and passwords of customers of the restaurant booking platform IRM-NG.
Bitdefender has published the latest research results from a cyber criminal campaign currently underway on the IRM-NG booking platform used in the hotel and hospitality industry. The attackers use vulnerabilities in the platform in combination with backdoors and techniques to bypass password validation on the end device and thus steal credit card data, passwords and customers' personal data.
Security vulnerability still exists
Bitdefender has not received any response from the manufacturer Resort Data Processing (RDP) to its information for months. The vulnerability still exists and users remain vulnerable. Bitdefender was able to trace the attackers back until the summer of 2022 and assign them to a special group. The group's tailored attack consists of multiple modules designed to blend into legitimate software and operate stealthily. The malware and other tools suggest that the group knows IRM-NG's inner workings very well and that this is likely not the first operation it has launched against this software.
Attackers can generate passwords themselves
The IRM-NG engine enables employees of the RDP manufacturer to log in to their customers' clients using a special administrator account - with password verification taking place on the end device and not on the manufacturer's servers. The password validation algorithm is located in the Dynamic Link Library (DLL) and, according to Bitdefender experts, is weak. Attackers can use this vulnerability to generate the daily password themselves and thus successfully log in to any account of the customer company.
Bitdefender recommendation
Bitdefender advises hospitality organizations using IRM-NG to increase vigilance and review IOCs from the research presented by Bitdefender. Defending against modern attacks like this should include a “defense-in-depth” architecture that includes threat prevention, detection and response through solutions like XDR/EDR or managed security services like MDR.
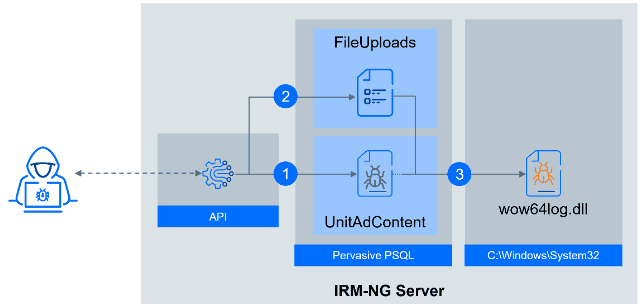
🔎 The hackers' approach: 1. The content of the webshell is uploaded to the database entry. 2. A new record is created with instructions for the file upload service. 3. The service saves the contents of a cell in a library in the System32 folder. (Image: Bitdefender)
About Bitdefender Bitdefender is a leading global provider of cybersecurity solutions and antivirus software, protecting over 500 million systems in more than 150 countries. Since it was founded in 2001, the company's innovations have consistently ensured excellent security products and intelligent protection for devices, networks and cloud services for private customers and companies. As the supplier of choice, Bitdefender technology is found in 38 percent of security solutions deployed around the world and is trusted and recognized by industry experts, manufacturers and customers alike. www.bitdefender.de
