
Cyber insurance is not just a question of company strategy, but also whether you get it at all. The new Sophos guide to cyber insurance helps management and IT managers in companies better understand the cyber insurance market. After all, there are unavoidable requirements that must be met in order to ensure that insurance is as economical as possible.
Companies often secure additional technical security through cyber insurance. Behind this strategy is, on the one hand, the knowledge of the danger of possibly backward in-house security and, on the other hand, a business calculation on the part of the management team.
Every second company affected by attacks
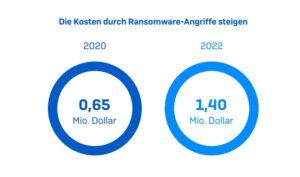
🔎 The costs of a cyber attack have increased on average from 0,65 to 1,40 million dollars (Image: Sophos).
What is clear is that in the latest Sophos State of Ransomware Report, 49 percent of those surveyed in Germany (70 percent in Austria and 60 percent in Switzerland) confirmed that there was data encryption in the company by ransomware. The risk exists. And it is also clear that cyber insurance can make the total costs of such an incident, which are many times the extortion amount, more bearable. After all, the global average total cost of recovery excluding the ransom payment after an attack is $1,82 million. The average ransom amount was $1,54 million, almost double the previous year's $812,380 million.
Ransoms over 1,5 million dollars – on average!
However, the costs of cyber insurance have risen sharply in recent years due to the large number of claims and the criteria for obtaining insurance cover are now major hurdles for companies. The new guide for cyber insurance from Sophos provides assistance and explains how companies can With modern cybersecurity you can get a better insurance status at cheaper premiums or a policy at all. In addition to current comparisons of whether insurance protection in different industries is covered within business insurance or as separate insurance, the costs of insurance services and the market for cyber insurance, Sophos provides practical tips for obtaining protection at good conditions.
Cyber insurance: four crucial aspects
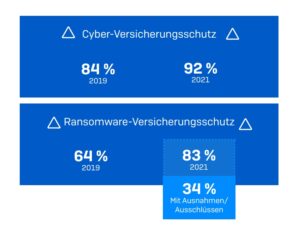
🔎 A survey of 5.600 IT decision-makers in medium-sized companies showed that 92% already have cyber insurance protection - compared to 84% in the previous year (Image: Sophos).
Multi-Factor Authentication (MFA)
A fundamental requirement is to establish multi-factor authentication (MFA) across the organization and for all applications. Insurers want to ensure that common security gaps are closed before they take on risks.
Endpoint Detection and Response (EDR) or Extended Detection and Response (XDR)
Advanced endpoint protection is the essential foundation for strong cyber defense. In addition, to prevent cutting-edge ransomware and security breaches (and therefore damage), it is important to proactively search for, analyze and respond to suspicious activity before cybercriminals can carry out their attack. EDR and XDR programs enable security professionals to detect and analyze potential compromises, eliminating complex cyberattacks before damage occurs. Most cyber insurers require EDR for insurance coverage.
Managed Detection and Response (MDR)
MDR is a 24/7 fully managed service provided by a team of security experts. These specialize in detecting and combating cyberattacks that pure technology solutions are powerless against. The service minimizes the risk and likelihood of having to claim insurance. Although managed detection and response (MDR) is not a mandatory requirement for insurers, companies that use MDR services are often considered premium customers because they pose the lowest risk.
Incident Response Plan
Preparation is the best strategy for preventing a cyberattack from becoming a widespread security incident. After a security breach, companies often find that an incident response plan would have saved many costs, problems and business interruptions. A detailed plan to mitigate the consequences of an incident reduces cyber risk and makes the company more attractive to insurance providers.
More at Sophos.com
About Sophos More than 100 million users in 150 countries trust Sophos. We offer the best protection against complex IT threats and data loss. Our comprehensive security solutions are easy to deploy, use and manage. They offer the lowest total cost of ownership in the industry. Sophos offers award-winning encryption solutions, security solutions for endpoints, networks, mobile devices, email and the web. In addition, there is support from SophosLabs, our worldwide network of our own analysis centers. The Sophos headquarters are in Boston, USA and Oxford, UK.
