
By law, companies in China - including foreign ones - are obliged to immediately report vulnerabilities in systems and errors in codes to a government agency. However, experts warn that China uses state-controlled hackers and could use the information about the vulnerabilities to gain almost unhindered access to companies' systems.
The Atlantic Council think tank has published a report analyzing the new Chinese regulation that requires companies to report security vulnerabilities and errors in code to a government Ministry of Industry and Information Technology (MIIT) within 48 hours. At the same time, the experts warn that China controls several hacker groups and can immediately use the information for attacks. The report is therefore entitled “How China is weaponizing software vulnerabilities”. In the analysis, the think tank's experts even assume that the current constant source of zero-day vulnerabilities goes back to the MIIT's Chinese database.
Many new zero-day vulnerabilities from MIIT database?
Chinese rules prohibit researchers from publishing information about vulnerabilities before a patch is available unless they coordinate with the product owner and the MIIT. Also publishing proof-of-concept code showing how a vulnerability is exploited is not allowed.
According to the report, the disclosure of the vulnerability to the Beijing Office of the 13th MSS Bureau is particularly concerning. Experts point out that the bureau has spent the last twenty years gaining early access to software vulnerabilities.
Hardly any sharing of ICS vulnerabilities
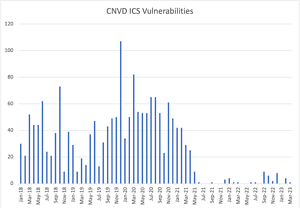
Since May 2021, there has been a near complete decline in publicly reported ICS vulnerabilities in China according to the CNVD database (Image: Sleight of Hand, Cary and Del Rosso, Atlantic Council).
The report also found that many vulnerabilities reported in the ICS (Industrial Control System) area are no longer being communicated to affected companies. Chinese state databases have shown almost no vulnerabilities in the ICS area since May 2021. Before that there were 40 to 80 or more vulnerabilities every month. As of May 2021, they are suddenly at 1 to 10. In comparison, the US CISA continues to have monthly ICS reports of over 100 vulnerabilities.
The experts point out that many foreign companies may not even be aware that their Chinese employees are reporting the vulnerabilities. After all, they might be punished if they circumvent Chinese law.
More at AtlanticCouncil.org
