Interest in Zero Trust has exploded recently, due in part to the catchy name and seemingly widespread use in the cybersecurity industry. Is it already time to talk about ZTNA 2.0?
Many organizations are struggling to manage the cyber risks associated with hybrid work and direct connectivity to applications. The new reality is that the attack surface has increased significantly as cyberattacks continue to grow in scale and sophistication. The “whack-a-mole” approach, using a new tool for each type of application or threat, makes security management and enforcement far too complex. With this in mind, Palo Alto Networks explains the need for an expanded Zero Trust approach: ZTNA 2.0.
Time for ZTNA 2.0 for enterprise
Most companies have found that the old and cumbersome VPN-based solutions just don't cut it anymore from a security and performance perspective. These traditional solutions have no concept of context and therefore do not understand how to apply application, user or device based least privilege access. Instead, they grant trusted access to entire network segments. In the world of hybrid working and cloud migration, legacy VPN is dead.
Zero Trust Network Access (ZTNA) approaches have emerged to address the challenges posed by legacy VPN. However, the first generation of products, dubbed ZTNA 1.0, has proven more dangerous than helpful in Palo Alto Networks' experience due to several critical limitations:
- Too much access is not Zero Trust: Only supports coarse-grained access controls and classifies applications based on L3/L4 network constructs such as IP addresses and port numbers. Therefore, ZTNA 1.0 offers far too much access, especially for applications using dynamic ports or IP addresses.
- Allow and Ignore: Once access to an application is granted, that communication is trusted forever. ZTNA 1.0 assumes that the user and the application will always behave loyally, which is a recipe for disaster.
- Poor Security: Supports only a subset of private applications and is unable to properly secure microservice-based, cloud-native applications. These are applications using dynamic ports such as voice and video applications, or server-initiated applications such as helpdesk and patching systems. Additionally, traditional ZTNA approaches completely ignore SaaS applications and offer little to no visibility or control over the data.
Clearly, ZTNA 1.0 fails to deliver on the promise of replacing legacy VPN, so a different approach is needed.
Introducing ZTNA 2.0
Palo Alto Networks believes it's time for a new approach. ZTNA 2.0 addresses the shortcomings of ZTNA 1.0 by providing:
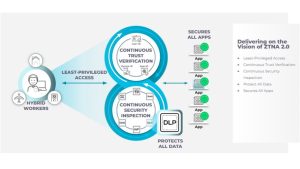
- Least Privilege Access: Achieved by identifying applications at Layer 7, enabling granular access control at the application and sub-application level, independent of network constructs such as IP and port numbers.
- Continuous Trust Checking: Once access to an application is granted, trust is continuously checked based on changes in device location, user and application behavior.
- Continuous security inspection: Deep and continuous inspection of all traffic, even on allowed connections, to prevent all threats, including zero-day threats.
- Protection of all data: Consistent data control of all applications used in the company, including personal applications and SaaS, with a single DLP policy.
- Security for all applications: Protection for all applications used in the company, including modern cloud-native applications, legacy private applications and SaaS applications. This includes applications using dynamic ports and applications using server-initiated connections.
Today, work is no longer a place employees go, but an activity they perform. At the height of the pandemic, many companies were focused on trying to scale their VPN infrastructure. When that didn't work, they quickly switched to ZTNA 1.0 only to find that this approach didn't meet their expectations. Palo Alto Networks believes ZTNA 2.0 is the necessary paradigm shift to overcome the existing limitations of ZTNA 1.0. It's the right architecture to support businesses over the long term.
More at PaloAltoNetworks.com
About Palo Alto Networks Palo Alto Networks, the global leader in cybersecurity solutions, is shaping the cloud-based future with technologies that transform the way people and businesses work. Our mission is to be the preferred cybersecurity partner and protect our digital way of life. We help you address the world's biggest security challenges with continuous innovation leveraging the latest breakthroughs in artificial intelligence, analytics, automation, and orchestration. By delivering an integrated platform and empowering a growing ecosystem of partners, we are the leaders in protecting tens of thousands of businesses across clouds, networks and mobile devices. Our vision is a world where every day is safer than the one before.