Ransomware attacks are becoming increasingly tricky. In addition to classic data encryption, attackers also look specifically for backups. With the right strategy, these attacks will come nowhere.
In 2020, the cost of ransomware attacks was more than $ 20 billion - more than twice as much as two years earlier. The average cost of downtime was $ 283.000 - per injured party. While ransomware attacks used to be widely spread and carried out without a defined target, there are now much more precise attacks in which the ransomware attack is sometimes only part of the attack.
The motivation behind a ransomware attack
Even in 2021, ransomware is and will remain an ever increasing threat. In 2020, a frightening record was set in the IT world with over 20.000 new reports of security vulnerabilities. One of the reasons for this is the new era of the home office, characterized by COVID-19, which led to a 50 percent increase in vulnerabilities in mobile devices and made companies more susceptible to cyberattacks.
However, companies and companies are no longer the only ones who have to fear ransomware attacks. Attacks on critical infrastructures have increased in recent months. For example, in a survey of 130 hospitals and healthcare organizations, almost half said they had to shut down their networks in the first half of 2021 due to ransomware. The ransom demands have also reached new highs.
$ 1,2 million per claim
Cyber insurance company Coalition found that the average ransom demand from policyholders rose to $ 2021 million per incident in the first half of 1,2, compared to "just" $ 450.000 in the first half of 2020.
The ransom note itself only accounts for a small part of the increasing total costs that arise from a ransomware attack. If you want to know what costs you should actually expect in an emergency, you should this summary look once.
Attack surfaces for ransomware
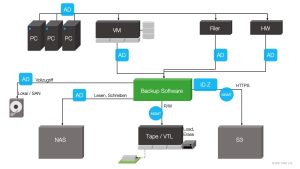
The classic IT infrastructure consists, for example, of computers, virtual machines, file servers and other hardware in the network. It contains a wide variety of data types that place different demands on the memory. Different security levels are formed from these different structures. Infrastructure that is not adequately secured by firewalls etc. provides entry gates for attackers.
Backups protect against data loss in the IT infrastructure. There are also various backup targets here, which are used to varying degrees depending on the type of data and requirements:
- Local / SAN: Storage connected directly to the backup server
- NAS: Storage connected to the backup server via the network
- Tape / VTL: A (virtual) tape library whose (real or virtual) data carriers can be ejected and in some cases physically removed (air gap)
- Object store (e.g. S3): Highly scalable storage that can be available locally (on premise) or at a service provider (cloud).
The “classic” ransomware attack via the infrastructure
In the case of a * ransomware attack via a PC *, it depends, among other things, on what rights the user has. Many companies often grant full admin rights as standard, which includes access to parts or all of IT, especially for management or department heads.
Assuming that the user has a high level of authorization, the ransomware can attack the following areas:
- The ransomware attacks and infects all devices that can be reached via the network. This begins with releases on other PCs, filers, releases on hardware components and can then spread to the backup server and its local and NAS storage. Then all data on the infected devices is encrypted.
- After this large-scale encryption, it is important to identify how the ransomware infiltrated the system and what exactly was infected and encrypted. In this scenario, backups via (virtual) tape libraries and object storage offer a way out of the situation.
In contrast to a classic ransomware attack, the targeted attack does not begin with the widespread distribution of the malware, but with the exploration of the customer's infrastructure. The key component to the highest possible infection is the Active Directory, through which all user rights are centrally managed.
How the ransomware attack then continues and how you can effectively protect your backup can be found in the full background report.
More at FASTLTA.com
About FAST LTA the FAST LTA is the specialist for secure secondary and long-term storage systems. The combination of durable and low-maintenance hardware, integrated software for data backup and on-site maintenance contracts with a term of up to 10 years ensure long-term, cost-effective storage of data from archive and backup applications. In-house developments such as local erasure coding, sealing using hardware WORM and efficient energy management help medium-sized customers to protect themselves against data loss through ransomware attacks and misconfiguration and to meet regulatory and legal requirements (GDPR). The Munich provider's solutions have proven themselves in thousands of installations in healthcare, public administration, film/TV/video and industry.