Most cyber criminals simply belong to criminal companies. And here, too, there is unwelcome competition. You can either use malware to access important information from other attackers or sell Malware-as-a-Service with a built-in back door so that you can access the data yourself. Zscaler looked at the backdoored malware against other cybercriminals.
Stealing information is fundamental for cyber gangs to gain access to systems and initiate larger malware campaigns against companies. In a recent analysis of the Prynt Stealer malware, Zscaler's ThreatLabz security researchers found that information theft is also a common occurrence among cybercriminals.
Information theft among cyber criminals
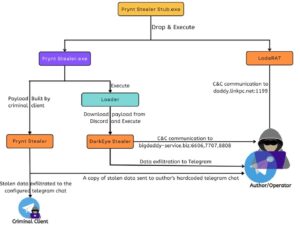
Malicious code designed to steal company information, such as the infostealer Prynt, is often configured by the creators via a builder and then sold to less experienced threat actors. When analyzing the Prynt Stealer, the security researchers discovered a backdoor that automatically forwards copies of the victims' exfiltrated data to a private Telegram chat. This chat is monitored by the builder's developers, who can use it to access the stolen data. In this way, the data from the stolen organizations gets into the hands of multiple threat actors, increasing the risk of one or more large-scale attacks.
Prynt Stealer steals from the competition
Using the Prynt Stealer, cyber criminals are able to collect credentials stored on compromised systems, including web browsers, VPN/FTP clients, and messaging and gaming applications. The stealer was programmed based on open source projects such as AsyncRAT and StormKitty. According to the security researchers' findings, the DarkEye and WorldWind malware families, which also steal information, are almost identical to Prynt Stealer.
Prynt Stealer is a relatively new information-stealing malware family written in .NET. Prynt Stealer is partially code copied directly from the repositories of the WorldWind and DarkEye variants and is believed to be from the same malware author. Many parts of the Prynt Stealer code, borrowed from other malware families, are not used but are present in the binary as unreachable code. The victim's captured files are forwarded to a Prynt operator's Telegram account. What the operator should not know, however, is that a copy of this data is also sent to the actual author of the malware via another embedded Telegram channel. DarkEye code is used as a back door.
Free backdoor malware
This approach has already been observed by malware authors in the past when malware was made available free of charge. The author benefits from the activities of cyber criminals who use his malware and infect companies with it. Since all Prynt Stealer samples discovered have the same Telegram channel embedded, this suggests the deliberate installation of the backdoor for monetization purposes, although some of the customers also pay for Prynt Stealer.
Conclusion: There is no honor among thieves
The free availability of source code for numerous malware families has made development and customization easier than ever for threat actors with little programming knowledge. As a result, many new malware families have emerged over the years based on popular open source malware projects such as NjRat, AsyncRAT, and QuasarRAT. The author of Prynt Stealer went one step further and added a backdoor to steal from his customers. To do this, he built a Telegram token and a chat ID into the malware. This tactic is by no means new and shows once again that there is no honor among thieves.
More at Zscaler.com
About Zscaler
Zscaler accelerates digital transformation so customers can become more agile, efficient, resilient, and secure. Zscaler Zero Trust Exchange protects thousands of customers from cyberattacks and data loss by securely connecting people, devices, and applications anywhere. The SSE-based Zero Trust Exchange is the world's largest inline cloud security platform, distributed across 150+ data centers around the world.