
Multiple attacks by ransomware groups are catching on - Hive, LockBit and BlackCat ransomware gangs attack the same network one after the other. The Sophos X-Ops Active Adversary Whitepaper shows: attacked company received three different ransomware reports for triple-encrypted files.
In the current Sophos X-Ops Active Adversary Whitepaper “Multiple Attackers: A Clear and Present Danger” reports Sophos that three known ransomware groups, Hive, LockBit and BlackCat, successively attacked the same network. The first two attacks occurred within two hours, with the third attack occurring two weeks later. Each ransomware group left its own ransom note and some of the files were triple encrypted.
3-way attack provides triple encryption
"It's bad enough to receive a single ransomware alert from a cybercriminal group, let alone three," said John Shier, senior security advisor at Sophos. “Multiple attackers create a whole new level of complexity for recovery, especially when files are triple encrypted. Cybersecurity with prevention, detection and response is critical for organizations of all sizes and types – no organization is immune from attack.”
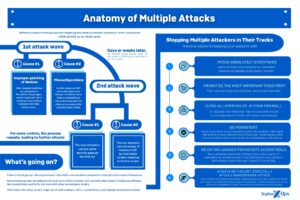
🔎 This is how a multiple attack by ransomware gangs like Hive, LockBit and BlackCat works (Image: Sophos).
The whitepaper describes other instances of overlapping cyberattacks, including cryptominers, remote access Trojans (RATs), and bots. If in the pastt multiple attackers targeting the same system, attacks typically spanned many months or years. The attacks described in the current Sophos whitepaper took place within a few days and weeks - in one case even simultaneously. Organizations are often attacked by attackers through the same vulnerable entry point into the network.
Competition and cooperation between cyber gangsters
Usually, cyber criminals compete, which makes it more difficult for multiple attackers to operate simultaneously. Mostly they eliminate their competitors on the same system. Today's RATs often point to the possibility of bot killing in criminal forums. In the attack involving the three ransomware groups, BlackCat was the last ransomware group on the system, not only deleting traces of its own activities, but also those of LockBit and Hive. In another case, a system was infected by LockBit ransomware. About three months later, members of Karakurt Team, a group with ties to Conti, managed to use the backdoor created by LockBit to steal data and demand ransom.
LockBit also allows members to collaborate
“By and large, ransomware groups do not appear to be openly hostile to one another. In fact, LockBit does not specifically prohibit its members from collaborating with competitors,” says Shier. "We have no evidence of collaboration. But it's possible for attackers to realize that in an increasingly competitive marketplace, there are only a limited number of targets to attack. Or they believe that the more pressure is applied to a target, such as multiple attacks, the more likely victims are to pay. They may have high-level discussions and make mutually beneficial agreements, such as one group encrypting the data and the other exfiltrating. At some point, these groups will have to decide whether to work together and take this approach further, or whether they want to be more competitive. But at the moment the playing field is open to multiple attacks from different groups.”
Unpatched vulnerabilities as gateways
In the attacks described in the white paper, most initial infections came from unpatched vulnerabilities. These include gaps in Log4Shell, ProxyLogon and ProxyShell or poorly configured or unsecured RDP (Remote Desktop Protocol) servers. In most cases involving multiple attackers, victims failed to effectively remediate the initial attack, leaving the door open to future cybercriminal activity. This made the same RDP misconfigurations as well as applications like RDWeb or AnyDesk an easily exploitable path for follow-up attacks. Unprotected or compromised RDP and VPN servers are among the most popular “deals” sold on the dark web.
Active Adversary Playbook
"In the current Active Adversary Playbook for 2021, Sophos is finding that businesses are being attacked simultaneously on multiple occasions and that this could be a growing trend," says Shier. "The fact that the increase in multiple attacks still has to be tracked on a case-by-case basis gives cybercriminals ample opportunity to move even further in this direction via the exploitable systems."
To learn more about multiple cyberattacks, including details on the criminal underground and practical advice on how to protect systems from such attacks, download the full Multiple Attackers: A Clear and Present Danger whitepaper from Sophos.
More at Sophos.com
About Sophos More than 100 million users in 150 countries trust Sophos. We offer the best protection against complex IT threats and data loss. Our comprehensive security solutions are easy to deploy, use and manage. They offer the lowest total cost of ownership in the industry. Sophos offers award-winning encryption solutions, security solutions for endpoints, networks, mobile devices, email and the web. In addition, there is support from SophosLabs, our worldwide network of our own analysis centers. The Sophos headquarters are in Boston, USA and Oxford, UK.
Matching articles on the topic
[starboxid=USER_ID] <>ff7f00
