New Sophos study reveals the growing threat of dropper-as-a-service. Disguised as pirated software, so-called droppers deliver entire bundles of malware, including programs for information theft, click fraud and much more.
Sophos has published a new study entitled “Fake Pirated Software Serves Up Malware Droppers as a Service”. The study describes how cyber criminals use droppers, i.e. programs that serve as Trojan horses for malware, to deliver a variety of harmful and unwanted content to people looking for hacked versions of popular business and consumer applications.
Fake Pirated Software Serves Up Malware Droppers as a Service
Paid download or dropper services have been around for a long time and the criminal operators earn good money with them. Recent research by Sophos suggests that this success can be attributed in part to the continued high demand for pirated applications. In addition, the chargeable services of this type enable even less qualified cyber criminals to carry out mass data theft or even cryptocurrency fraud at minimal cost. Dropper-as-a-service providers are effectively maximizing profits by bundling a range of malicious or unwanted content into droppers and showering victims with a range of malicious applications in a single download.
Working from home also increases the risk
In the past 18 months, millions of people have worked from home, often using personal devices, adding to the risk of malicious dropper downloads for businesses. At the same time, the far more lucrative corporate goals are also within reach for cyber criminals, who normally do not have the competence for complex attacks. For example, the investigations by SophosLabs discovered droppers that contain backdoors such as Glupteba and theft malware such as Raccoon Stealer and Crypto Bot. Fortunately, in terms of security, malware delivered by droppers is easy to distinguish from safe software by either its signature or its behavior. However, malicious packages are often contained in encrypted archives. Most security technologies do not detect malicious files until they are extracted.
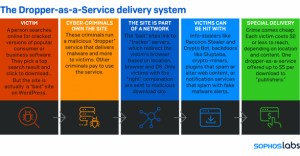
How Dropper-as-a-Service works
SophosLabs recently published a study on the Raccoon Stealer, which was distributed as part of a malicious code package by a Dropper-as-a-Service. Following this study, the researchers analyzed how these dropper services convey their various data. The following diagram shows what happens when the download of a supposedly pirated copy is clicked, but in reality it is a disguised malware dropper:
Protection against dropper malware
Sophos recommends that companies review their security software, settings and policies, and ensure that malicious and unwanted downloads are detected and blocked. This also includes a robust approach to web filtering. The malware hidden in a dropper package may not be discovered until it is unzipped. At this point, however, it can already be on the network. A good web filter not only checks regular downloads, but also the encrypted network traffic. According to a Sophos study, more than half of malware now uses Transport Layer Security (TLS) encryption for communication. Web filters also protect companies and their employees from connecting to dangerous or untrustworthy servers by blocking malicious domains and URLs.
Companies should also complement network security with up-to-date endpoint protection that includes behavioral detection capabilities on all devices used by employees for remote access. For example, Sophos Firewall and Intercept X for Endpoints have all of these features and more, including protection against ransomware.
More at Sophos.com
About Sophos More than 100 million users in 150 countries trust Sophos. We offer the best protection against complex IT threats and data loss. Our comprehensive security solutions are easy to deploy, use and manage. They offer the lowest total cost of ownership in the industry. Sophos offers award-winning encryption solutions, security solutions for endpoints, networks, mobile devices, email and the web. In addition, there is support from SophosLabs, our worldwide network of our own analysis centers. The Sophos headquarters are in Boston, USA and Oxford, UK.