In the ransomware wave, which, according to the BSI, affects thousands of servers worldwide, including a mid-three-digit number of German companies, the attackers are targeting server farms - so-called ESXi servers - and thus the heart of every IT landscape. Outdated and unpatched VMware ESXi servers that still work with the February 2021 vulnerability were specifically attacked.
According to the BSI - Federal Office for Information Security, thousands of servers running VMware's ESXi virtualization solution were infected with ransomware and many were also encrypted in a widespread global attack. The regional focus of the attacks on the VMware ESXi servers was on France, the USA, Germany and Canada - other countries are also affected. The perpetrators took advantage of a long-known vulnerability. The vulnerability itself – which is listed as CVE-2021-21974 and according to CVSS with a severity of 8.8 as "high" - there has been a patch from the manufacturer since February 2021.
This is what Trend Micro says about the ESXi server attack
“We see time and time again that companies are not prepared for such third-party problems. There is a regular patch process for Microsoft, but not for third-party manufacturers, such as VMware in this case. Because the number of patches does not justify creating a separate process for it. Additionally, companies don't just shut down their server farm to install a single patch. Attackers are aware of the difficulties their victims face and therefore often exploit vulnerabilities that are not based on Microsoft technology.
ESXi vulnerability already reported to VMware in October 2020
In fact, only about 30 percent of the vulnerabilities used by attackers rely on software from the tech giant. It is not uncommon for hackers to actively exploit unpatched software vulnerabilities. According to research by Trend Micro, around 86 percent of all companies worldwide have such gaps. Trend Micro's Zero Day Initiative reported the vulnerability, identified as CVE-2021-21974 and rated "high" by CVSS with a severity of 8.8, to VMware in October 2020 and then jointly published a Responsible Disclosure of the vulnerability (responsible disclosure)" says Richard Werner, Business Consultant at Trend Micro.
This is what Check Point says about the ESXi server attack
“The outages that have occurred in the past few days can be precisely traced back to this ransomware attack, which is a growing threat not only in European countries like France and Italy, but worldwide. Back in July of last year, Check Point Research's ThreatCloud reported a 59 percent year-over-year increase in ransomware globally. With this increase and the attack reported yesterday, it is appropriate to reiterate that preventing cyber threats must be a top priority for businesses and organizations.
Even non-Windows machines are now at risk
This massive attack on ESXi servers is also considered one of the largest cyber attacks ever reported on non-Windows machines. What makes the situation even more worrying is the fact that until recently, ransomware attacks were limited to Windows-based machines. The attackers have recognized how important Linux servers are for the systems of institutions and organizations,” says Lothar Geuenich, VP Central Europe / DACH at Check Point Software Technologies.
That's what Barracuda says about the ESXi server attack

🔎 Barracuda Networks: Stefan van der Wal, Consulting Solutions Engineer, EMEA, Application Security (Image: Barracuda Networks).
“The reported widespread ransomware attacks on unpatched VMware ESXi systems in Europe and elsewhere appear to have exploited a vulnerability that was patched in 2021. This shows how important it is to update critical software infrastructure systems in an absolutely timely manner. It is not always easy for companies to update software. In the case of this patch, for example, companies have to temporarily deactivate significant parts of their IT infrastructure. But it's far better to put up with this than get hit by a potentially malicious attack.
Organizations using ESXi should update to the latest version immediately
Securing the virtual infrastructure is critical. Virtual machines can be an attractive target for ransomware as they often run business-sensitive services or functions - and a successful attack could cause widespread disruption. It is particularly important to ensure that access to a virtual machine's management console is protected and cannot, for example, simply be accessed via a compromised account on the corporate network,” said Stefan van der Wal, Consulting Solutions Engineer, EMEA, Application Security at Barracuda Networks.
This is what Artic Wolf says about the ESXi server attack
Despite reports that successful ransomware attacks are declining, the global attack on servers across Europe and North America shows that ransomware is still a real threat to businesses and organizations worldwide. By exploiting a vulnerability in VMWare, criminals were able to attack a major supplier that supplies multiple industries and even countries. So it's safe to assume that the attack will continue to cause widespread disruption to thousands of people for some time to come.
Businesses should constantly review current security posture
“In the first half of 2022, more than half of all security incidents were caused by exploiting external vulnerabilities. A trend that can be observed: Threat actors are increasingly targeting organizations of all sizes – particularly via known vulnerabilities. Therefore, it is more important than ever for organizations to get their cybersecurity fundamentals right, e.g. B. through consistent and regular patching.
This means working with experts to identify the right technology, training employees in the right application and constantly reviewing the current security situation. In this way, they can ensure that they are in the best possible position to react to new threats and protect themselves in the best possible way. Also, in the event that certain systems go down, contingency plans are critical to allow organizations to continue operating,” said Dan Schiappa, Chief Product Officer at Arctic wolf.
That's what Tehtris says about the ESXi server attack
TEHTRIS has published an analysis of the ESXiArgs ransomware attack that became known over the weekend. The security experts came to the conclusion that the attacks were preceded by a number of activities before the actual attack took place. For their investigation, the security researchers analyzed activities related to port 427 in particular, which is of great importance in the current attacks.
ESXiArgs ransomware: Attacks not just since the weekend
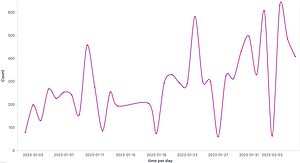
The ESXiArgs cyber campaign got its name because it creates an .args file for each encrypted document. Thanks to its worldwide network of honeypots, Tehtris was able to determine that the attack that became known over the weekend did not just begin a few days ago. The timeline below, based on data from Tehtris since January 1, 2023, shows that there was a spike in attacks on port 10 as early as January 24 and 427. These activities then picked up again in early February.
Some of the malicious IPs that Tehtris is monitoring in this context in its honeypot network tried to stay under the radar before February 3rd. While they were very discreet by only making a single call, they reached a large number of the honeypots. Looking at the global honeypot panel shows that most of the incoming attacks on port 427 target the eastern part of the US, the northeastern part of Asia-Pacific and western Europe, and at practically the same level. Further investigation results including an analysis of the IP addresses from which the attacks originate can be found in Tehtris' latest blog post.