To be competitive these days, companies need to keep pace with the latest technological trends. Without the parallel development of a security infrastructure and a clear process for responding to attacks, however, these technologies could become the fatal vector for cyber threats.
In the event of a cyber attack, a strong incident response plan can get a business back up and running with minimal damage. A good playbook is of great help in setting up the incident response process.
According to a study carried out by IBM and Ponemon, data theft costs the company concerned on average 3,92 million dollars. These costs can vary based on how quickly a company detects and responds to a data breach.
The 2020 Data Breach Investigations Report from Verizon found that while most data breaches in 2019 lasted days or less, a quarter of the cases dragged on for months or more. Containment, on the other hand, took about the same time on average.
Overall, the numbers in the report show an improvement in detecting and responding to data breaches compared to previous years. However, the report also suggests that this improvement could be due to the fact that more breaches detected by managed security service providers (MSSPs) were included in their investigations.
Organizations should of course strive to prevent the break-ins. At the same time, however, preparing for such incidents and creating procedures to shorten the duration of a data breach is an essential and realistic approach to dealing with current threats.
Prepare for the threats
Knowing what a company can expect is the first step in preparing for and responding to potential cyberattacks. In the past, threats were much simpler and largely defined by the technologies they exploited. But now, as organizations move to more advanced network and data infrastructures, the attack surface is larger and the impact of the threats has increased.
The Security report for 2019 from Trend Micro highlights the complexity and persistence of today's threats. Ransomware attacks are increasingly targeting high-profile targets, with criminals developing fewer new families. In 2019 there were 95 new ransomware families, less than half compared to 2018 (222). Phishing-related activities also decreased.
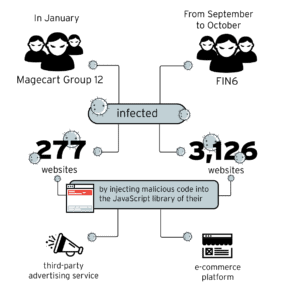
In 2019, there were a number of high profile attacks on e-commerce sites like Magecart Group 12 and FIN6, infecting thousands of online stores in order to steal customer payment information.
The above threats illustrate the security gaps in the technologies used today. They also show how trends and weaknesses in industries, devices or platforms shape the threat landscape. Organizations have a variety of fundamentals to cover when introducing new applications and software, improving operations, and driving innovation. In addition to understanding the current threats, employees should also have a deep understanding of all of the technologies used by their organization.
While multilayered protection can help detect and prevent cyberattacks, all employees who are responsible for maintaining the company's infrastructure should also have a knowledge of how to react to a break-in and an active attack.
Incident Response
Threats attacking corporate lines of defense require an effective incident response strategy. It is the process or plan that organizations use as a guide in managing and containing a breach or cyber attack.
The goal of Incident Response is to get the company back on track after an attack. This includes identifying and qualifying the threat that has overcome their defenses. An incident also implies that the organization's preventive mechanisms have failed and need to be strengthened.
A distinctive feature of incident response is that the response can be successful without having to identify the threat actor behind the attack. Incident Response takes place “live” or during an ongoing attack with the intention of stopping it. In contrast, computer forensics, for example, is done after the fact and can go into depth because the threat has decreased.
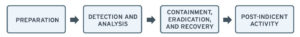
There are two widely accepted incident response frameworks: NIST (National Institute of Standards and Technology) and SANS (SysAdmin, Audit, Network, and Security). They are very similar to each other and cover a broad base, from preparing for an attack to making sure the incident does not repeat itself.
GLUTEN
NIST
More on this in the blog at Trendmicro.de
About Trend Micro As one of the world's leading providers of IT security, Trend Micro helps create a secure world for digital data exchange. With over 30 years of security expertise, global threat research, and constant innovation, Trend Micro offers protection for businesses, government agencies, and consumers. Thanks to our XGen™ security strategy, our solutions benefit from a cross-generational combination of defense techniques optimized for leading-edge environments. Networked threat information enables better and faster protection. Optimized for cloud workloads, endpoints, email, the IIoT and networks, our connected solutions provide centralized visibility across the entire enterprise for faster threat detection and response.