
Trend Micro, one of the world's leading providers of cybersecurity solutions, publishes a new research report on cryptomining. The report details how cybercriminals are compromising and misusing corporate cloud infrastructures. Again and again, different groups even fight for control of the affected systems.
The report shows that threat actors are increasingly looking for and exploiting vulnerable entities. Among other things, they use brute-forcing of SecureShell (SSH) credentials to compromise cloud resources for cryptocurrency mining. Victims often have outdated cloud software in the cloud environment, lack of cloud security hygiene, or insufficient knowledge of cloud service protection. This makes it easier for attackers to gain access to the systems.
Large investments in cloud computing
Investments in cloud computing have skyrocketed during the pandemic. The simple deployment of the new systems means that many cloud applications are online longer than necessary - often unpatched and misconfigured.
Malicious cryptomining has various negative consequences for the companies affected: On the one hand, the additional computing workload threatens to slow down important cloud services. On the other hand, the operating costs for each infected system increase by up to 600 percent. In addition, cryptomining can be a harbinger of an even more serious compromise. Many professional threat actors use mining software to generate additional revenue before online shoppers buy access to ransomware, stolen data, and more from them.
Operating costs for infected systems increase by 600 percent
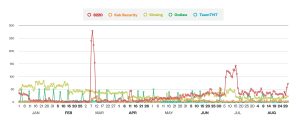
An analysis of detection statistics for attacks by cryptomining groups. The January-August 2021 report shows interesting trends. These groups are attacking the cloud and fighting over the system (Image: Trend Micro).
“Just a few minutes of compromise can bring profits to the attackers. Therefore, we observe a continuous battle for cloud CPU resources. It's like a real-world 'capture-the-flag' game, where the playing field is the company's cloud infrastructure,” said Richard Werner, Business Consultant at Trend Micro. “Threats like this require unified, platform-based security to ensure attackers have nowhere to hide. The right platform helps IT teams see their attack surface, assess risk, and choose the right protection without adding significant overhead.”
Trend Micro researchers detail the activities of several cryptomining threat groups, including the following groups and their modus operandi:
- Outlaw compromises Internet of Things (IoT) devices and Linux cloud servers by exploiting known vulnerabilities or performing brute force attacks on SSH.
- TeamTNT uses vulnerable software to compromise hosts. The group then steals credentials for additional services in order to access new hosts and abuse their misconfigured services.
- Kinsing installs an XMRig kit for mining Monero, removing all other miners from the affected system in the process.
- 8220 competes with Kinsing for the same systems. They often evict each other from a host and then install their own cryptocurrency miners.
- Kek Security is associated with IoT malware and running botnet services.
To mitigate the threat of cryptocurrency mining attacks in the cloud, Trend Micro recommends the following security measures for businesses:
- Make sure systems are up to date and only required services are running.
- Use firewalls, intrusion detection systems (IDS)/intrusion prevention systems (IPS), and cloud endpoint security to limit and filter network traffic for known malicious hosts.
- Avoid configuration errors with the help of cloud security posture management tools.
- Monitor traffic to and from cloud instances and filter out domains associated with known mining pools.
- Implement cost-based rules for monitoring open ports, changes in Domain Name System (DNS) routing, and CPU resource utilization.
About Trend Micro As one of the world's leading providers of IT security, Trend Micro helps create a secure world for digital data exchange. With over 30 years of security expertise, global threat research, and constant innovation, Trend Micro offers protection for businesses, government agencies, and consumers. Thanks to our XGen™ security strategy, our solutions benefit from a cross-generational combination of defense techniques optimized for leading-edge environments. Networked threat information enables better and faster protection. Optimized for cloud workloads, endpoints, email, the IIoT and networks, our connected solutions provide centralized visibility across the entire enterprise for faster threat detection and response.
