New Barracuda study reveals geographic and network warning signs of phishing attacks. The country email originated from and the number of countries it was routed through on its way to its final destination are major warning signs of a phishing attack.
A new study by Barracuda in collaboration with Columbia University analyzed the geolocation and network infrastructure of more than 2 billion emails sent in January 2020, including 218.000 phishing emails. The research showed that phishing emails were more likely to come from certain countries in parts of Eastern Europe, Central America, the Middle East, and Africa.
2 billion emails = almost 220.000 phishing emails
They are also more likely to be routed through a greater number of locations than harmless emails. A surprising number of attacks have also originated from large, legitimate cloud providers. This is believed to be because the attackers were able to compromise legitimate servers and / or email accounts hosted by these providers.
In the following, a closer look at the influence of geography and network infrastructure on phishing attacks as well as on solutions that help to identify, block and repel these attacks.
Geographical and network characteristics of phishing attacks
In phishing attacks, attackers use social engineering tactics to trick their victims into revealing personal information such as usernames, passwords, credit card numbers or bank details. Phishing detection largely focuses on the content of phishing emails and the behavior of the attacker. However, as phishing attacks become more complex, those who want to protect themselves from these attacks must employ increasingly sophisticated methods.
Barracuda examined the network-level characteristics of phishing emails because they are more persistent and more difficult for attackers to manipulate. The security researchers extracted IP addresses from the "Received" fields of the e-mail headers, which record information about the servers passed through during transmission. Examining this data revealed the path a phishing email takes between its sender and recipients. The analysis revealed three key findings:
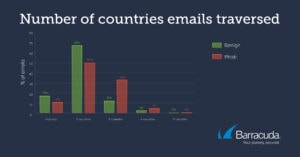
Phishing emails are routed through at least 2 countries
Over 80 percent of benign emails go through two or fewer countries. In contrast, this is the case for just over 60 percent of phishing emails. The number of different countries an email goes through can therefore serve as a good indicator of phishing detection.
Countries more likely to be phishing in parts of Eastern Europe, Central America, the Middle East, and Africa
The security researchers have also determined the phishing probability for different countries. For this purpose, the country of the sender was identified with the geolocation data and the phishing probability for each country was calculated as follows:
Phishing probability = number of phishing emails from the country / total number of emails from the country
Some countries with high levels of phishing have an extremely low chance of phishing. For example, 129.369 phishing emails were sent from the USA in the data set, but the USA only has a phishing probability of 0,02 percent. In general, most countries had a phishing chance of 10 percent or less. Senders who produced a higher volume of phishing emails (more than 1.000 emails in the data set) with a higher phishing probability came from the following countries or territories (in descending order):
- Lithuania
- Latvia
- Serbia
- Ukraine
- Russia
- Bahamas
- Puerto Rico
- Colombia
- Iran
- Palestine
- Kazakhstan
While it doesn't make sense to block all email traffic from countries with a high risk of phishing, it may be a good idea to flag emails from those countries for further analysis.
Phishing emails: often via legitimate cloud providers
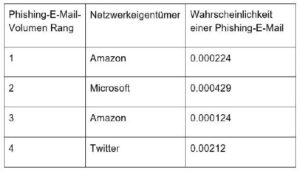
Top 4 networks: Probability that a certain e-mail from the network is a phishing e-mail (graphic: Barracuda).
The networks with the highest number of phishing attacks surprisingly belong to large cloud providers. This is to be expected as they also have the highest total volume of emails sent. With such networks, the likelihood that a particular email is a phishing email is very low. It is likely that most of the attacks emanating from these networks originated from compromised email accounts or servers that the attackers were able to access the credentials for.
It was also shown that some of the phishing attackers with the highest volume (by network), who also have a high phishing probability, still come from networks that belong to cloud service providers (Rackspace, Salesforce). These networks have less total email traffic than the top networks, but still send a significant amount of phishing emails. Therefore, the likelihood that an email from them is malicious is much higher (Table 2).
Best practices for protecting against phishing attacks
1. Solutions that use artificial intelligence
Cyber criminals are adapting their tactics to bypass email gateways and spam filters. Therefore, it is important to deploy a solution that detects and protects against spear phishing attacks, including brand impersonation, business email compromise, and account takeover. Organizations should adopt a solution that doesn't rely solely on finding malicious links or attachments. A technology that uses machine learning to analyze normal communication patterns within the company can detect anomalies that could indicate an attack.
2. Implementation of account takeover protection
Your security strategy should be thought beyond external email messages because some of the most harmful and compelling spear phishing attacks are sent from compromised internal accounts. Attackers should therefore be prevented from using the company as a base for spear phishing campaigns. A security technology should be used that uses artificial intelligence to detect when accounts have been compromised and that is capable of remedial action in real time by warning users and removing malicious emails sent from compromised accounts.
3. Improving safety awareness through training
Users should be kept informed of the latest spear phishing attacks and tactics. Companies should make sure that their employees can detect attacks and know how to report them to the IT department immediately. Phishing simulations for email, voicemail, and SMS are recommended to train users to detect cyberattacks, test the effectiveness of the training, and identify the most vulnerable users.
Phishing will continue to be one of the most popular tactics used by cyber criminals. With the above measures, however, companies can adequately defend themselves against the flood of these attacks and significantly reduce the risk of a security breach.
[starboxid=5]