The IDC study "Building the Case for a Virtuous Cycle in Cybersecurity" calls for the introduction of a "virtuous cycle" model in its analysis for more cyber resilience in order to close critical security gaps. The study also highlights that AI may be the solution for improved detection and response.
The biggest challenge for cybersecurity professionals is managing the large amounts of data they receive from various alert systems. They struggle to prioritize and contextualize these effectively. They also struggle to identify the key actions needed to effectively contain threats and vulnerabilities. That shows the one published by Darktrace IDC Study "Building the Case for a Virtuous Cycle in Cybersecurity". Also important: Only 29% of those surveyed can test their IT environments against current threats.
The most important results of the study at a glance
- Constantly changing attack vectors make preparing for cyber attacks more difficult. Only 31% of respondents are very confident that their tools will continuously adapt to new configurations.
- 65% believe pen tests provide a snapshot of limited value as results quickly become stale. So there is a lack of dynamic test options.
- 76% believe that visualizing attack paths is of medium or high importance. Yet only 29% are very confident they have a robust mechanism in place to test their environments against the current threat vectors.
- Only 24-31% of organizations are able to continuously conduct preventative exercises such as pen testing and attack surface assessment.
In its evaluation, IDC calls for the introduction of a “virtuous cycle” model in order to close critical security gaps. It should include prevention, detection, response and recovery. In addition, IDC recommends a multi-layered approach that includes maintaining a security posture, proactively managing access and assets, monitoring the environment, and backup and disaster recovery.
AI solutions increase responsiveness
The study also highlights that AI is the solution for improved detection and response, as well as continuous monitoring. AI also plays an essential role in the "Virtuous Cycle" as it can detect subtle changes in behavior within a network. "It is clear from this study that only a holistic approach can improve readiness for organizations," said Christopher Kissel, research vice president of IDC's Security & Trust Products. “The solution lies in creating a virtuous cycle with the help of AI to implement a defense system for the entire company. This should be able to continuously stress test environments, respond immediately, and determine if remedial actions are working.”
“Security teams don't need more data, they need clear prioritization and intelligent automation to ease the burden. The report shows that in concrete terms,” says John Allen, VP of Cyber Risk and Compliance at Darktrace. “Security professionals are overwhelmed with vulnerabilities and can't fix them all in time. At Darktrace, we provide a Cyber AI Loop that enables continuous visibility, prioritizes sensible actions for security teams, and hardens vulnerabilities. In this way, we help security teams to work proactively.”
Background of the study
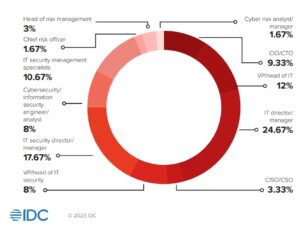
In July 2022, IDC surveyed senior security professionals at 300 companies in Europe and the United States. The aim was to determine what difficulties they encounter when implementing preventive security measures and what gaps they need to close in their security structures. All companies involved have more than 500 employees. The people interviewed were mostly IT directors, IT managers, IT security management specialists, CIOs and CTOs.
More at Darktrace.com
About Darktrace
Darktrace, a global leader in artificial intelligence for cybersecurity, protects businesses and organizations with AI technology from cyberattacks. Darktrace's technology registers atypical traffic patterns that indicate possible threats. In doing so, it recognizes novel and previously unknown attack methods that are overlooked by other security systems.