
A new Exabeam study shows: Corona is driving IT security into the cloud. The home office has accelerated the use of cloud-based security tools.
Exabeam presented the results of a survey of security practitioners on the introduction and use of cloud-based security tools. This latest survey was carried out as a comparative sample of a study carried out in March 2020. This allows direct conclusions to be drawn about the influence of the corona crisis on the use of cloud-based security tools.
Unsurprisingly, there was an increase in the use of the cloud for parts of IT security: at the beginning of the year, 75 percent of those surveyed were already using the cloud. In the comparison survey, this value rose to 90 percent. Accordingly, the companies that had planned the deployment had implemented these plans at the beginning of the pandemic. 90 percent of those surveyed agree that their companies opted for cloud-based security at the right time. Despite the numerous advantages, companies are also well aware of the dangers of using the cloud for IT security.
Concerns about relocating IT security to the cloud are increasing
Data protection has always been a concern for many companies. The increased use of the cloud has apparently increased these concerns even further: while 30 percent of respondents were previously concerned about data protection, this value rose to 56 percent in the latest survey. The possibility of unauthorized access is also seen as a greater danger. The percentage rose here from 16 to 31 percent.
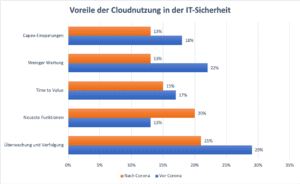
Exabeam Study: One of the more and more important advantages of using the cloud is “access to the latest functions”.
However, when weighing the benefits against potential dangers, the benefits seem to outweigh the risks. The current study shows that almost half of the organizations surveyed (44 percent) now also use cloud-based security products to protect their financial data. This is a dramatic increase from Exabeam's previous study, which found that only 12 percent of companies had their financial information protected in this way.
Highly risky or well equipped?
Despite this increased use of cloud-based security tools, 86 percent still consider the move "risky" or "highly risky." These concerns are in sharp contrast to 87 percent of respondents who consider themselves “well equipped” to orchestrate cloud-based migration. 79 percent of those surveyed said they had either good or very good insight into their cloud applications. As the pandemic fuels the shift of the workforce to the remote office, 84 percent of companies have significantly improved their efforts to increase visibility of cloud-based applications. 26 percent of respondents believe they have “very good insight” into cloud-based applications.
Access to new functions is becoming more important

Sam Humphries, Exabeam: "The consequences of the corona crisis left organizations with no choice but to jump on the cloud bandwagon."
There has been an interesting shift in the various benefits of moving to a cloud-based model. Almost all the benefits of using the cloud were seen as less important. In contrast, the value for “access to the latest functions” rose noticeably from 13 to 20 percent. Obviously, this advantage is a decisive reason for many organizations to use the cloud, since security tools in the cloud offer more flexible access to new technologies than solutions used in the data center.
"The sudden, and for many unexpected, shift to remote working in March paved the way for cloud-based security solutions, as organizations had to migrate critical business data to the cloud almost overnight," said Samantha Humphries, security strategist at Exabeam. "Regardless of their concerns, the consequences of the corona crisis left waiting organizations with no choice but to jump on the cloud train."
More on this at Exabeam.com
About Exabeam Exabeam stands for Smarter SIEM ™. Exabeam enables companies to more efficiently detect, investigate, and respond to cyberattacks so their security and insider threat teams can operate more efficiently. Security organizations no longer have to live with inflated prices, missed distributed attacks and unknown threats or manual investigations and countermeasures. With the Exabeam Security Management Platform, security analysts can collect unlimited log data, use behavioral analysis to detect attacks and automate the response to incidents, both on site and in the cloud. Exabeam Smart Timelines, sequences of user and entity behavior created through machine learning, further reduce the time and specialization required to identify attacker tactics, techniques and procedures. Exabeam is privately funded by Aspect Ventures, Cisco Investments, Icon Ventures, Lightspeed Venture Partners, Norwest Venture Partners, Sapphire Ventures and well-known security investor Shlomo Kramer. More information is available at www.exabeam.com. Follow Exabeam on Facebook, Twitter, YouTube or LinkedIn.
